diff --git a/blog/2020-08-10-the-league-of-entropy-launches-drand-v1-0-to-becom.md b/blog/2020-08-10-the-league-of-entropy-launches-drand-v1-0-to-becom.md
index 3fb1b46c..a5e1b9dc 100644
--- a/blog/2020-08-10-the-league-of-entropy-launches-drand-v1-0-to-becom.md
+++ b/blog/2020-08-10-the-league-of-entropy-launches-drand-v1-0-to-becom.md
@@ -68,10 +68,10 @@ In 2019, Cloudflare, EPFL, the University of Chile, Kudelski Security, and Proto
With the LoE Main Network upgrade, new partners have joined, increasing robustness and quality of service. Current members include:
-- [EPFL Center for Digital Trust (C4DT)](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/EPFL%20Center%20for%20Digital%20Trust%20(C4DT)%20dc94bcdadab64950aa1e6bc96cb1e39a.md)
-- [ChainSafe Systems](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/ChainSafe%20Systems%20480ac8864a33408dae64fad706c38a8e.md)
-- [c**·**Labs](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/c%C2%B7Labs%208125559f2fb44804b9e6ca63da70f6b6.md)
-- [Cloudflare](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Cloudflare%2012bbcd90be5f4e42af18599f65019e7e.md)
+- [EPFL Center for Digital Trust (C4DT)](https://drand.love/dc94bcdadab64950aa1e6bc96cb1e39a)
+- [ChainSafe Systems](https://drand.love/480ac8864a33408dae64fad706c38a8e)
+- [c**·**Labs](https://drand.love/8125559f2fb44804b9e6ca63da70f6b6)
+- [Cloudflare](https://drand.love/12bbcd90be5f4e42af18599f65019e7e)
- [Emerald Onion](https://emeraldonion.org/)
- [EPFL](https://www.epfl.ch/labs/dedis/)
- [Ethereum Foundation](https://ethereum.foundation/)
diff --git a/blog/2020-08-10-the-league-of-entropy-launches-drand-v1-0.md b/blog/2020-08-24-drand-v1-0-two-weeks-in.md
similarity index 94%
rename from blog/2020-08-10-the-league-of-entropy-launches-drand-v1-0.md
rename to blog/2020-08-24-drand-v1-0-two-weeks-in.md
index 34428594..40fecdae 100644
--- a/blog/2020-08-10-the-league-of-entropy-launches-drand-v1-0.md
+++ b/blog/2020-08-24-drand-v1-0-two-weeks-in.md
@@ -10,8 +10,8 @@ Two weeks ago, we announced the launch of drand v1.0, the League of Entropy prod
+- [The League of Entropy launches drand v1.0 to become the Internet’s first production-grade, publicly verifiable randomness beacon!](/blog/the-league-of-entropy-launches-drand), drand, Aug 10
- [The League of Entropy Launches Production Drand Network, Providing the First Publicly Verifiable Distributed Randomness Beacon](https://www.notion.so/League-of-Entropy-Launches-Production-drand-Network-dfc17d24f35d4558b6fd909276d573c1?pvs=21), League of Entropy press release, Aug 10 (picked up by [Yahoo! Finance](https://finance.yahoo.com/news/league-entropy-launches-production-drand-140000595.html) and others)
-- [The League of Entropy launches drand v1.0 to become the Internet’s first production-grade, publicly verifiable randomness beacon!](The%20League%20of%20Entropy%20launches%20drand%20v1%200%20to%20becom%202577496887ce4d88bf89358d0df69ac7.md), drand, Aug 10
- [How a Decentralized Randomness Beacon Could Boost Cryptographic Security](https://www.notion.so/How-a-Decentralized-Randomness-Beacon-Could-Boost-Cryptographic-Security-c880532146ff464eb953d388292b126e?pvs=21), CoinDesk, Aug 10
- [Tierion Joins the League of Entropy — Replaces NIST Randomness Beacon with Drand in Chainpoint Proofs](https://www.notion.so/Tierion-joins-LoE-replaces-NIST-Beacon-with-drand-in-Chainpoint-639248133237404cbc0ecf1dc42e598c?pvs=21), Tierion, Aug 10
- [Liga de la Entropía entra en etapa de producción.](https://www.clcert.cl/2020/08/11/drand_uchile.html), University of Chile, Aug 11 (in Spanish)
diff --git a/blog/2021-01-11-the-league-of-entropy-welcomes-quantum-resistant-ledger-qrl.mdx b/blog/2021-01-11-the-league-of-entropy-welcomes-quantum-resistant-ledger-qrl.mdx
index 90221d6b..133c1ef4 100644
--- a/blog/2021-01-11-the-league-of-entropy-welcomes-quantum-resistant-ledger-qrl.mdx
+++ b/blog/2021-01-11-the-league-of-entropy-welcomes-quantum-resistant-ledger-qrl.mdx
@@ -6,7 +6,7 @@ tags: [league-of-entropy, new-members,news]
date: 2021-01-11
---
-On Wednesday, December 16, 2020, The League of Entropy, running an [upgraded version of drand](https://github.com/drand/drand/releases/tag/v1.2.5), proudly welcomed The [Quantum Resistant Ledger](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Quantum%20Resistant%20Ledger%20b3e60c968098435790c3718f85ed3057.md) (QRL) to its list of esteemed members. QRL is an enterprise-grade blockchain platform that is secure from the quantum computing advances of tomorrow, as verified by external audits. The [QRL Foundation](https://qrl.foundation/), a not-for-profit organization, supports the research and development of open-source post-quantum blockchain solutions.
+On Wednesday, December 16, 2020, The League of Entropy, running an [upgraded version of drand](https://github.com/drand/drand/releases/tag/v1.2.5), proudly welcomed The [Quantum Resistant Ledger][QUANTUM] (QRL) to its list of esteemed members. QRL is an enterprise-grade blockchain platform that is secure from the quantum computing advances of tomorrow, as verified by external audits. The [QRL Foundation](https://qrl.foundation/), a not-for-profit organization, supports the research and development of open-source post-quantum blockchain solutions.
{/* truncate */}
diff --git a/blog/2021-08-09-drand-celebrates-one-year-as-a-randomness-service.mdx b/blog/2021-08-09-drand-celebrates-one-year-as-a-randomness-service.mdx
index 14586ebe..14f3b902 100644
--- a/blog/2021-08-09-drand-celebrates-one-year-as-a-randomness-service.mdx
+++ b/blog/2021-08-09-drand-celebrates-one-year-as-a-randomness-service.mdx
@@ -13,7 +13,7 @@ drand, the distributed randomness beacon that aims to serve as a foundational ra
We have two reasons to celebrate today:
- drand is celebrating its first anniversary since the launch of a significant upgrade to the mainnet on August 10, 2020, that enabled it to be used as a production-grade network! Drand has served as critical off-chain infrastructure for [Filecoin](https://filecoin.io/) (the world’s largest decentralized storage network) since its mainnet launch in Oct 2020 and several other projects in Web3 and beyond.
-- drand has been running smoothly without disruptions since its launch in July 2020 and recently completed 1M rounds - a significant milestone for this distributed randomness service for Web3 and the Internet at large! We would like to congratulate [](https://www.notion.so/89fecb56737044e5bdfbbb3f6864a422?pvs=21) for achieving this milestone, and thank them for operating a reliable randomness service for the Internet ([The League of Entropy](https://www.notion.so/The-League-of-Entropy-1e76674b75e249699445799c5083fe78?pvs=21) is a collection of independent randomness beacon providers who work together to produce collective, publicly verifiable, unbiased, and unpredictable random values at fixed intervals).
+- drand has been running smoothly without disruptions since its launch in July 2020 and recently completed 1M rounds - a significant milestone for this distributed randomness service for Web3 and the Internet at large! We would like to congratulate [](https://drand.love/89fecb56737044e5bdfbbb3f6864a422) for achieving this milestone, and thank them for operating a reliable randomness service for the Internet ([The League of Entropy](https://drand.love/1e76674b75e249699445799c5083fe78) is a collection of independent randomness beacon providers who work together to produce collective, publicly verifiable, unbiased, and unpredictable random values at fixed intervals).
There are also several reasons that *you* should be excited about the future of drand, which include:
diff --git a/blog/2021-09-13-the-value-of-drand-part-1-of-2.md b/blog/2021-09-13-the-value-of-drand-part-1-of-2.md
index 2e70f4aa..ca063a3e 100644
--- a/blog/2021-09-13-the-value-of-drand-part-1-of-2.md
+++ b/blog/2021-09-13-the-value-of-drand-part-1-of-2.md
@@ -1,6 +1,6 @@
---
slug: "the-value-of-drand-part-1-of-2"
-title: "The Value of drand (Part 1 of 2)"
+title: "Discover The Value of drand (Part 1 of 2)"
authors: [yolan]
tags: [league-of-entropy]
date: 2021-09-13
@@ -10,11 +10,11 @@ date: 2021-09-13
-[The League of Entropy](https://www.notion.so/The-League-of-Entropy-1e76674b75e249699445799c5083fe78?pvs=21) (LoE) is a consortium of independent, and diverse organizations that partner together to operate a decentralized, bias-resistant, publicly verifiable, and reliable randomness beacon, called **drand**! The consortium was originally formed in 2019, and is currently supported by 16 member organizations that includes: [Cloudflare](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Cloudflare%2012bbcd90be5f4e42af18599f65019e7e.md), [EPFL Decentralized & Distributed Systems Lab (DeDiS)](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/EPFL%20Decentralized%20&%20Distributed%20Systems%20Lab%20(DeDi%20e855b8f643d4475aa89a47252e6623d9.md), [Universidad de Chile](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Universidad%20de%20Chile%2027708a6027104c3ba708e2d8d7508a66.md), [Kudelski Security](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Kudelski%20Security%20d800657770494c6cb39cffb5480407a4.md), [Protocol Labs](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Protocol%20Labs%209e18324379574803918146d996c24df5.md), [ChainSafe Systems](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/ChainSafe%20Systems%20480ac8864a33408dae64fad706c38a8e.md), [c**·**Labs](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/c%C2%B7Labs%208125559f2fb44804b9e6ca63da70f6b6.md), [EPFL Center for Digital Trust (C4DT)](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/EPFL%20Center%20for%20Digital%20Trust%20(C4DT)%20dc94bcdadab64950aa1e6bc96cb1e39a.md), [Emerald Onion](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Emerald%20Onion%20e22d8bdb07ef4198b283d0436bcc9cf4.md), [Ethereum Foundation](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Ethereum%20Foundation%20184fc01bc464488c9570eb543d6c386a.md), [PTisp](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/PTisp%20f8fa38c9c36d4b4bbbb40fe785e9ae12.md), [Tierion](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Tierion%205b38e1b289f44e9d87498eddb788d38f.md), [University College London](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/University%20College%20London%20af818bec61a542daa950596f01fddf09.md), and [Quantum Resistant Ledger](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Quantum%20Resistant%20Ledger%20b3e60c968098435790c3718f85ed3057.md).
+[The League of Entropy](https://drand.love/1e76674b75e249699445799c5083fe78) (LoE) is a consortium of independent, and diverse organizations that partner together to operate a decentralized, bias-resistant, publicly verifiable, and reliable randomness beacon, called **drand**! The consortium was originally formed in 2019, and is currently supported by 16 member organizations that includes: [Cloudflare][CLOUDFLARE], [EPFL Decentralized & Distributed Systems Lab (DeDiS)][DEDIS], [Universidad de Chile][CHILE], [Kudelski Security](https://drand.love/d800657770494c6cb39cffb5480407a4), [Protocol Labs][PROTOCOL], [ChainSafe Systems][CHAINSAFE], [c**·**Labs][CLABS], [EPFL Center for Digital Trust (C4DT)][C4DT], [Emerald Onion][EMERALD], [Ethereum Foundation][ETHEREUM], [PTisp][PTISP], [Tierion][TIERION], [University College London][UCL], and [Quantum Resistant Ledger][QUANTUM].
-drand recently celebrated 1 year of undisrupted service, and completed 1M+ rounds of randomness (emitted at 30s intervals). You can read more about drand’s recent achievements in our recent [blog post](drand%20celebrates%20One%20Year%20as%20a%20Randomness%20Service!%20c66f0a909f034eae8f9bdc1b69d4014b.md).
+drand recently celebrated 1 year of undisrupted service, and completed 1M+ rounds of randomness (emitted at 30s intervals). You can read more about drand’s recent achievements in our recent [blog post](/blog/drand-celebrates-one-year-as-a-randomness-service).
-As a free, and not-for-profit service, [The League of Entropy](https://www.notion.so/The-League-of-Entropy-1e76674b75e249699445799c5083fe78?pvs=21) (LoE) members believe in the value of randomness as a foundational Internet service, and commit resources in order to maintain, and operate the drand network for public use. In order to gain insights into the motivations, and vision for drand shared by the LoE members, we reached out to them with a few questions. In this blog post, we summarize answers shared by five members of the LoE (we will share responses from other members through future blog posts).
+As a free, and not-for-profit service, [The League of Entropy](https://drand.love/1e76674b75e249699445799c5083fe78) (LoE) members believe in the value of randomness as a foundational Internet service, and commit resources in order to maintain, and operate the drand network for public use. In order to gain insights into the motivations, and vision for drand shared by the LoE members, we reached out to them with a few questions. In this blog post, we summarize answers shared by five members of the LoE (we will share responses from other members through future blog posts).
We hope you enjoy reading these insights, and come and join the LoE to grow and strengthen the network! The larger the LoE, the stronger the security, and reliability guarantees that drand provides, as any biasing attempt becomes significantly more difficult!
@@ -22,54 +22,69 @@ We hope you enjoy reading these insights, and come and join the LoE to grow and
### **“Why is drand important as a protocol for the next generation of the Internet in your opinion?”**
-[Cloudflare](../The-League-of-Entropy-1e76674b75e249699445799c5083fe78/League-Partners-89fecb56737044e5bdfbbb3f6864a422/Cloudflare-12bbcd90be5f4e42af18599f65019e7e.md): When the League of Entropy was founded the only available public randomness beacons were provided by individual entities, which require a strong trust model for applications and a potential single point of failure. Drand provides an elegant solution to this problem as a distributed, verifiable randomness beacon, allowing applications to only trust an uncorrupted threshold of parties in the system rather than a single entity. Trusted public randomness has many applications in the modern Internet; for example, it can help to provide auditability of lotteries or transparency in leader election processes.
+[Cloudflare][CLOUDFLARE]: When the League of Entropy was founded the only available public randomness beacons were provided by individual entities, which require a strong trust model for applications and a potential single point of failure. Drand provides an elegant solution to this problem as a distributed, verifiable randomness beacon, allowing applications to only trust an uncorrupted threshold of parties in the system rather than a single entity. Trusted public randomness has many applications in the modern Internet; for example, it can help to provide auditability of lotteries or transparency in leader election processes.
-[Kudelski Security](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Kudelski%20Security%20d800657770494c6cb39cffb5480407a4.md): For us, randomness is about fairness. When solutions are fair, they build trust among communities and participants. Public, verifiable randomness is a building block enabling fairness and trust for many protocols and blockchains.
+[Kudelski Security][KUDELSKI]: For us, randomness is about fairness. When solutions are fair, they build trust among communities and participants. Public, verifiable randomness is a building block enabling fairness and trust for many protocols and blockchains.
-[Quantum Resistant Ledger](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Quantum%20Resistant%20Ledger%20b3e60c968098435790c3718f85ed3057.md): We see decentralization of all aspects of society as crucial to the evolution of a globalized world. Randomness, the hidden component of so many systems, plays a key role in security and trust.
+[Quantum Resistant Ledger][QUANTUM]: We see decentralization of all aspects of society as crucial to the evolution of a globalized world. Randomness, the hidden component of so many systems, plays a key role in security and trust.
-[EPFL Decentralized & Distributed Systems Lab (DeDiS)](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/EPFL%20Decentralized%20&%20Distributed%20Systems%20Lab%20(DeDi%20e855b8f643d4475aa89a47252e6623d9.md): The quality of the random numbers used in cryptographic systems directly impacts on the security of a system. Randomness plays a key role in establishing secure connections, generating cryptographic key pairs and system’s authentication. As an Internet infrastructure level service, Drand can provide true, verifiable randomness to applications.
+[EPFL Decentralized & Distributed Systems Lab (DeDiS)][EPFL]: The quality of the random numbers used in cryptographic systems directly impacts on the security of a system. Randomness plays a key role in establishing secure connections, generating cryptographic key pairs and system’s authentication. As an Internet infrastructure level service, Drand can provide true, verifiable randomness to applications.
-[Tierion](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Tierion%205b38e1b289f44e9d87498eddb788d38f.md): Security and trust are fundamental to a free and open Internet. Drand helps developers build secure systems that don’t rely on trusted authorities.
+[Tierion][TIERION]: Security and trust are fundamental to a free and open Internet. Drand helps developers build secure systems that don’t rely on trusted authorities.
---
### **“Why did you decide to join the League of Entropy? What value do you see in drand that is important for your mission (what convinced you to join)?”**
-[Cloudflare](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Cloudflare%2012bbcd90be5f4e42af18599f65019e7e.md): Cloudflare is on a mission to help build a better Internet, and that means making it more secure, fast, and reliable for everyone. We see drand and the League of Entropy as foundational Internet infrastructure, and with that we are committed to supporting the project. We aim to be on the forefront of deploying next-generation cryptographic protocols and are excited to support this application of threshold cryptography that solves a real-world problem.
+[Cloudflare][CLOUDFLARE]: Cloudflare is on a mission to help build a better Internet, and that means making it more secure, fast, and reliable for everyone. We see drand and the League of Entropy as foundational Internet infrastructure, and with that we are committed to supporting the project. We aim to be on the forefront of deploying next-generation cryptographic protocols and are excited to support this application of threshold cryptography that solves a real-world problem.
-[Kudelski Security](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Kudelski%20Security%20d800657770494c6cb39cffb5480407a4.md): We come at this from a bit of a different angle. We are a group of cryptographers who help customers secure their systems. This work involves everything from complex cryptography to public blockchains. In our work, we see lots of customers having a difficult time handling randomness in their applications. This is dangerous because randomness underpins the security of so many cryptographic functions. This makes us obsessed with sources of randomness both public and private.
+[Kudelski Security][KUDELSKI]: We come at this from a bit of a different angle. We are a group of cryptographers who help customers secure their systems. This work involves everything from complex cryptography to public blockchains. In our work, we see lots of customers having a difficult time handling randomness in their applications. This is dangerous because randomness underpins the security of so many cryptographic functions. This makes us obsessed with sources of randomness both public and private.
-[Quantum Resistant Ledger](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Quantum%20Resistant%20Ledger%20b3e60c968098435790c3718f85ed3057.md): With a shared vision of decentralization, the aims and objectives of both the QRL Foundation and the League of Entropy are very much aligned. It is important to us that we support innovations at the cutting edge of security.
+[Quantum Resistant Ledger][QUANTUM]: With a shared vision of decentralization, the aims and objectives of both the QRL Foundation and the League of Entropy are very much aligned. It is important to us that we support innovations at the cutting edge of security.
-[EPFL Decentralized & Distributed Systems Lab (DeDiS)](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/EPFL%20Decentralized%20&%20Distributed%20Systems%20Lab%20(DeDi%20e855b8f643d4475aa89a47252e6623d9.md): Drand was born at our offices. Originally, it was a development by Nicolas Gailly, at that time a PhD student at the DEDIS lab at EPFL, with contributions from Philipp Jovanovic and under the supervision of Bryan Ford.
+[EPFL Decentralized & Distributed Systems Lab (DeDiS)][EPFL]: Drand was born at our offices. Originally, it was a development by Nicolas Gailly, at that time a PhD student at the DEDIS lab at EPFL, with contributions from Philipp Jovanovic and under the supervision of Bryan Ford.
Many protocols need a reliable, unbiased, and publicly-verifiable source of randomness. The DEDIS lab started work on decentralized randomness at Yale. Prof. Ford continued this work when he moved the lab to EPFL in 2015. As part of this mission, the DEDIS lab @ EPFL developed the crypto library Kyber, which provides all the major components to implement an efficient, distributed randomness generation protocol. The DEDIS lab is proud of contributing not just to the foundations, but also to the infrastructure providing public randomness.
-[Tierion](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Tierion%205b38e1b289f44e9d87498eddb788d38f.md): In 2017 Tierion announced its collaboration with the National Institute of Standards and Technology (NIST) to use the NIST Randomness Beacon to prove a timestamp proof was created between two points in time. Over time, development on the NIST Randomness Beacon slowed down and NIST experienced intermittent reliability issues. We began searching for a replacement and decided drand was by far the best option.
+[Tierion][TIERION]: In 2017 Tierion announced its collaboration with the National Institute of Standards and Technology (NIST) to use the NIST Randomness Beacon to prove a timestamp proof was created between two points in time. Over time, development on the NIST Randomness Beacon slowed down and NIST experienced intermittent reliability issues. We began searching for a replacement and decided drand was by far the best option.
---
### **“How you use drand in your setup, infrastructure or application?”**
-[Tierion](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Tierion%205b38e1b289f44e9d87498eddb788d38f.md): We use drand to prove each [**Chainpoint proof](https://tierion.com/chainpoint)** was created between two points in time. Every 30 seconds drand publishes a random value which is injected into each Chainpoint Proof. Since drand’s random values can’t be known before they are published, we can assert that each Chainpoint proof was created after the timestamp of the drand value.
+[Tierion][TIERION]: We use drand to prove each [**Chainpoint proof](https://tierion.com/chainpoint)** was created between two points in time. Every 30 seconds drand publishes a random value which is injected into each Chainpoint Proof. Since drand’s random values can’t be known before they are published, we can assert that each Chainpoint proof was created after the timestamp of the drand value.
---
### **“Where would you like to see drand in 2 years from now?”**
-[Cloudflare](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Cloudflare%2012bbcd90be5f4e42af18599f65019e7e.md): Continue to have more partners join the network with a focus on stability and operational resilience to ultimately strengthen the system, and to see continued growth in client adoption. Cloudflare is proud to be part of this, and we hope to see continued success of the network.
+[Cloudflare][CLOUDFLARE}]: Continue to have more partners join the network with a focus on stability and operational resilience to ultimately strengthen the system, and to see continued growth in client adoption. Cloudflare is proud to be part of this, and we hope to see continued success of the network.
-[Kudelski Security](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Kudelski%20Security%20d800657770494c6cb39cffb5480407a4.md): Quite simply, our hope is that more projects adopt drand. The more people learn about the project and where it can be used, the better.
+[Kudelski Security][KUDELSKI]: Quite simply, our hope is that more projects adopt drand. The more people learn about the project and where it can be used, the better.
-[Quantum Resistant Ledger](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Quantum%20Resistant%20Ledger%20b3e60c968098435790c3718f85ed3057.md): First and foremost, we hope the resilience displayed so far continues. Over time, we hope that broadening geographical, and network topology grants ongoing assurance to solutions, projects and ultimately consumers.
+[Quantum Resistant Ledger][QUANTUM]: First and foremost, we hope the resilience displayed so far continues. Over time, we hope that broadening geographical, and network topology grants ongoing assurance to solutions, projects and ultimately consumers.
-[EPFL Decentralized & Distributed Systems Lab (DeDiS)](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/EPFL%20Decentralized%20&%20Distributed%20Systems%20Lab%20(DeDi%20e855b8f643d4475aa89a47252e6623d9.md): First of all, we would love to see drand scale to thousands of participants by deploying the scalability techniques that we have been studying, e.g. in [**RandHound and RandHerd**](https://eprint.iacr.org/2016/1067.pdf). Second, we'd like Drand usage to grow and be leveraged in a fully asynchronous consensus protocol, a path we're exploring in our current work on [**Que Sera Consensus [FIX]**](https://drand.love/blog/2021/09/14/the-value-of-drand/%E2%80%8B%E2%80%8Bhttps://arxiv.org/abs/2003.02291). Finally, we imagine Drand empowering proof of stake, and proof of personhood mechanisms in open member consensus protocols to handle lotteries, committee elections, and similar applications.
+[EPFL Decentralized & Distributed Systems Lab (DeDiS)][EPFL]: First of all, we would love to see drand scale to thousands of participants by deploying the scalability techniques that we have been studying, e.g. in [**RandHound and RandHerd**](https://eprint.iacr.org/2016/1067.pdf). Second, we'd like Drand usage to grow and be leveraged in a fully asynchronous consensus protocol, a path we're exploring in our current work on [**Que Sera Consensus [FIX]**](https://drand.love/blog/2021/09/14/the-value-of-drand/%E2%80%8B%E2%80%8Bhttps://arxiv.org/abs/2003.02291). Finally, we imagine Drand empowering proof of stake, and proof of personhood mechanisms in open member consensus protocols to handle lotteries, committee elections, and similar applications.
-[Tierion](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Tierion%205b38e1b289f44e9d87498eddb788d38f.md): We’d like to see drand become a dial-tone for randomness that’s reliably available to any application connected to the Internet.
+[Tierion][TIERION]: We’d like to see drand become a dial-tone for randomness that’s reliably available to any application connected to the Internet.
---
*The League of Entropy evaluates, votes on, and onboards new members quarterly. If you want to be a part of the first production-grade distributed randomness beacon and help provide publicly verifiable randomness as a service, contact us at leagueofentropy@googlegroups.com. We are looking for enthusiastic teams with experience running secure production services who are interested in operating drand nodes and relays. We also encourage you to check out the drand GitHub repository for details.*
---
+
+[CLOUDFLARE]: https://drand.love/12bbcd90be5f4e42af18599f65019e7e
+[DEDIS]: https://drand.love/e855b8f643d4475aa89a47252e6623d9
+[CHILE]: https://drand.love/27708a6027104c3ba708e2d8d7508a66
+[KUDELSKI]: https://drand.love/d800657770494c6cb39cffb5480407a4
+[PROTOCOL]: https://drand.love/9e18324379574803918146d996c24df5
+[CHAINSAFE]: https://drand.love/480ac8864a33408dae64fad706c38a8e
+[CLABS]: https://drand.love/8125559f2fb44804b9e6ca63da70f6b6
+[C4DT]: https://drand.love/dc94bcdadab64950aa1e6bc96cb1e39a
+[EMERALD]: https://drand.love/e22d8bdb07ef4198b283d0436bcc9cf4
+[EMERALD]: https://drand.love/184fc01bc464488c9570eb543d6c386a
+[PTISP]: https://drand.love/f8fa38c9c36d4b4bbbb40fe785e9ae12
+[TIERION]: https://drand.love/5b38e1b289f44e9d87498eddb788d38f
+[UCL]: https://drand.love/af818bec61a542daa950596f01fddf09
+[QUANTUM]: https://drand.love/b3e60c968098435790c3718f85ed3057
diff --git a/blog/2021-10-27-the-value-of-drand-part-2-of-2.md b/blog/2021-10-27-the-value-of-drand-part-2-of-2.md
index 0dbc46ce..e92d1cad 100644
--- a/blog/2021-10-27-the-value-of-drand-part-2-of-2.md
+++ b/blog/2021-10-27-the-value-of-drand-part-2-of-2.md
@@ -6,68 +6,84 @@ tags: [league-of-entropy]
date: 2021-10-27
---
-*This blog post covers the second set of responses we received from League of Entropy members on our question: “What’s the value of drand for your organization and why do you support it”? We hope you enjoyed [**the first part**](The%20Value%20of%20drand%20(Part%201%20of%202)%200cc0bb5ecb6d471da62152370180701b.md) as much as we did.*
+*This blog post covers the second set of responses we received from League of Entropy members on our question: “What’s the value of drand for your organization and why do you support it”? We hope you enjoyed [**the first part**](/blog/the-value-of-drand-part-1-of-2) as much as we did.*
-*As a reminder, [The League of Entropy](https://www.notion.so/The-League-of-Entropy-1e76674b75e249699445799c5083fe78?pvs=21) (LoE) is a consortium of independent, and diverse organizations that partner together to operate a publicly verifiable, decentralized, bias-resistant, and reliable randomness beacon, called **drand**! The consortium was originally formed in 2019, and is currently supported by 16 member organizations that include: [Cloudflare](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Cloudflare%2012bbcd90be5f4e42af18599f65019e7e.md), [EPFL Decentralized & Distributed Systems Lab (DeDiS)](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/EPFL%20Decentralized%20&%20Distributed%20Systems%20Lab%20(DeDi%20e855b8f643d4475aa89a47252e6623d9.md), [Universidad de Chile](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Universidad%20de%20Chile%2027708a6027104c3ba708e2d8d7508a66.md), [Kudelski Security](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Kudelski%20Security%20d800657770494c6cb39cffb5480407a4.md), [Protocol Labs](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Protocol%20Labs%209e18324379574803918146d996c24df5.md), [ChainSafe Systems](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/ChainSafe%20Systems%20480ac8864a33408dae64fad706c38a8e.md), [c**·**Labs](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/c%C2%B7Labs%208125559f2fb44804b9e6ca63da70f6b6.md), [EPFL Center for Digital Trust (C4DT)](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/EPFL%20Center%20for%20Digital%20Trust%20(C4DT)%20dc94bcdadab64950aa1e6bc96cb1e39a.md), [Emerald Onion](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Emerald%20Onion%20e22d8bdb07ef4198b283d0436bcc9cf4.md), [Ethereum Foundation](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Ethereum%20Foundation%20184fc01bc464488c9570eb543d6c386a.md), [PTisp](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/PTisp%20f8fa38c9c36d4b4bbbb40fe785e9ae12.md), [Tierion](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Tierion%205b38e1b289f44e9d87498eddb788d38f.md), [University College London](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/University%20College%20London%20af818bec61a542daa950596f01fddf09.md), and the [Quantum Resistant Ledger](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Quantum%20Resistant%20Ledger%20b3e60c968098435790c3718f85ed3057.md) Foundation.*
+*As a reminder, [The League of Entropy][LOE] (LoE) is a consortium of independent, and diverse organizations that partner together to operate a publicly verifiable, decentralized, bias-resistant, and reliable randomness beacon, called **drand**! The consortium was originally formed in 2019, and is currently supported by 16 member organizations that include: [Cloudflare][CLOUDFLARE], [EPFL Decentralized & Distributed Systems Lab (DeDiS)][DEDIS], [Universidad de Chile][CHILE], [Kudelski Security][KUDELSKI], [Protocol Labs][PROTOCOL], [ChainSafe Systems][CHAINSAFE], [c**·**Labs][CLABS], [EPFL Center for Digital Trust (C4DT)][C4DT], [Emerald Onion][EMERALD], [Ethereum Foundation][EMERALD], [PTisp][PTISP], [Tierion][TIERION], [University College London][UCL], and the [Quantum Resistant Ledger][QUANTUM] Foundation.*
---
### **“Why is drand important as a protocol for the next generation of the Internet in your opinion?”**
-[Universidad de Chile](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Universidad%20de%20Chile%2027708a6027104c3ba708e2d8d7508a66.md): We think it is important to promote decentralized services on the Internet. Nowadays, a lot of vital services on the Internet are in control of a single entity, who has the capacity to shut it down and control a lot of the communications and processes that occur every single day. Drand comes to establish a new way of providing vital services on the Internet, allowing that several independent organizations share the control and power of a randomness beacon. We are currently running a centralized beacon, but we think that our collaboration with the drand project is a must-do for our organization.
+[Universidad de Chile][CHILE]: We think it is important to promote decentralized services on the Internet. Nowadays, a lot of vital services on the Internet are in control of a single entity, who has the capacity to shut it down and control a lot of the communications and processes that occur every single day. Drand comes to establish a new way of providing vital services on the Internet, allowing that several independent organizations share the control and power of a randomness beacon. We are currently running a centralized beacon, but we think that our collaboration with the drand project is a must-do for our organization.
-[ChainSafe Systems](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/ChainSafe%20Systems%20480ac8864a33408dae64fad706c38a8e.md): We have seen many interesting blockchain applications limited by the availability of reliable, true randomness. Drand presents a novel solution that can enable the next generation of blockchain-based applications.
+[ChainSafe Systems][CHAINSAFE]: We have seen many interesting blockchain applications limited by the availability of reliable, true randomness. Drand presents a novel solution that can enable the next generation of blockchain-based applications.
-[EPFL Center for Digital Trust (C4DT)](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/EPFL%20Center%20for%20Digital%20Trust%20(C4DT)%20dc94bcdadab64950aa1e6bc96cb1e39a.md): Verifiable randomness greatly simplifies many decentralized protocols. By shifting some trust to Drand, we move to a more stable, better audited and less resource intensive solution for making network-wide choices.
+[EPFL Center for Digital Trust (C4DT)][C4DT]: Verifiable randomness greatly simplifies many decentralized protocols. By shifting some trust to Drand, we move to a more stable, better audited and less resource intensive solution for making network-wide choices.
-[c**·**Labs](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/c%C2%B7Labs%208125559f2fb44804b9e6ca63da70f6b6.md): Randomness is essential for security in protocols and allows building tools that enable large-scale confidence and fast user experience, down to individuals. Unbiasable, unpredictable and fast randomness even more so, and now that the league of entropy exists, it is safer to claim the public has access to such randomness.
+[c**·**Labs][CLABS]: Randomness is essential for security in protocols and allows building tools that enable large-scale confidence and fast user experience, down to individuals. Unbiasable, unpredictable and fast randomness even more so, and now that the league of entropy exists, it is safer to claim the public has access to such randomness.
-[Protocol Labs](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Protocol%20Labs%209e18324379574803918146d996c24df5.md): Just like many of the protocols that our computers use every day, such as the Domain Name System (DNS) and the Network Time Protocol (NTP), we believe the Internet also needs to have a randomness protocol that is publicly verifiable, bias-resistant and distributed, that is, not controlled by a single organization. Drand ticks all of those boxes!
+[Protocol Labs][PROTOCOL]: Just like many of the protocols that our computers use every day, such as the Domain Name System (DNS) and the Network Time Protocol (NTP), we believe the Internet also needs to have a randomness protocol that is publicly verifiable, bias-resistant and distributed, that is, not controlled by a single organization. Drand ticks all of those boxes!
---
### **“Why did you decide to join the League of Entropy? What value do you see in drand that is important for your mission (what convinced you to join)?”**
-[Universidad de Chile](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Universidad%20de%20Chile%2027708a6027104c3ba708e2d8d7508a66.md): Because we were (and still are) running a randomness beacon on our own (Random UChile) and we wanted to stay in touch with all the beacons projects around the world. We thought that contributing to a decentralized beacon was a great opportunity to cooperate with other universities and organizations interested in the same subject as we do. We are convinced that randomness beacons must be a foundational part of the Internet; there must exist a lot of beacons with different configurations, algorithms, and geographic footprint around the world. We want to contribute to that idea in the best possible way.
+[Universidad de Chile][CHILE]: Because we were (and still are) running a randomness beacon on our own (Random UChile) and we wanted to stay in touch with all the beacons projects around the world. We thought that contributing to a decentralized beacon was a great opportunity to cooperate with other universities and organizations interested in the same subject as we do. We are convinced that randomness beacons must be a foundational part of the Internet; there must exist a lot of beacons with different configurations, algorithms, and geographic footprint around the world. We want to contribute to that idea in the best possible way.
-[ChainSafe Systems](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/ChainSafe%20Systems%20480ac8864a33408dae64fad706c38a8e.md): We joined LoE primarily because it is used within the Filecoin protocol. As the builders of the secondary implementation of the Filecoin protocol, as well as several user-level applications, we understand the critical nature of drand and are eager to support its development.
+[ChainSafe Systems][CHAINSAFE]: We joined LoE primarily because it is used within the Filecoin protocol. As the builders of the secondary implementation of the Filecoin protocol, as well as several user-level applications, we understand the critical nature of drand and are eager to support its development.
-[EPFL Center for Digital Trust (C4DT)](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/EPFL%20Center%20for%20Digital%20Trust%20(C4DT)%20dc94bcdadab64950aa1e6bc96cb1e39a.md): We support many projects created at EPFL and are historically close to DEDIS. Helping such a publicly funded project take off and see how well it behaves in the wild is important for us.
+[EPFL Center for Digital Trust (C4DT)][C4DT]: We support many projects created at EPFL and are historically close to DEDIS. Helping such a publicly funded project take off and see how well it behaves in the wild is important for us.
-[c**·**Labs](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/c%C2%B7Labs%208125559f2fb44804b9e6ca63da70f6b6.md): We have been impressed by the quality of drand and the team behind it, and believe that the LoE is capable of creating a secure randomness beacon, and so we'd like to be a part of it.
+[c**·**Labs][CLABS]: We have been impressed by the quality of drand and the team behind it, and believe that the LoE is capable of creating a secure randomness beacon, and so we'd like to be a part of it.
-[Protocol Labs](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Protocol%20Labs%209e18324379574803918146d996c24df5.md): drand was masterminded by one of PL’s research engineers, Nicolas Gaily, during his time at DEDIS-EPFL. Turning research results to production systems is at the heart of PL’s mission. PL is one of the founding partners of the League of Entropy, as we firmly believe that distributed randomness should be a foundational protocol for the Internet. drand is also a fundamental component of the Filecoin network, which is one of the key projects that PL supports.
+[Protocol Labs][PROTOCOL]: drand was masterminded by one of PL’s research engineers, Nicolas Gaily, during his time at DEDIS-EPFL. Turning research results to production systems is at the heart of PL’s mission. PL is one of the founding partners of the League of Entropy, as we firmly believe that distributed randomness should be a foundational protocol for the Internet. drand is also a fundamental component of the Filecoin network, which is one of the key projects that PL supports.
---
### **“How you use drand in your setup, infrastructure or application?”**
-[Universidad de Chile](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Universidad%20de%20Chile%2027708a6027104c3ba708e2d8d7508a66.md): We are not currently using drand in our setup, but we plan to include drand output as a new external source for our own randomness beacon ([**Random UChile**](https://random.uchile.cl/)).
+[Universidad de Chile][CHILE]: We are not currently using drand in our setup, but we plan to include drand output as a new external source for our own randomness beacon ([**Random UChile**](https://random.uchile.cl/)).
-[c**·**Labs](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/c%C2%B7Labs%208125559f2fb44804b9e6ca63da70f6b6.md): We've used drand as the randomness beacon in [**Plumo**](https://medium.com/celoorg/celo-sets-sights-on-becoming-fastest-evm-chain-through-collaboration-with-mysten-labs-e88b426aee83), a SNARK-based ultralight client, and have collaborated with the LoE and have been inspired by the techniques that are used to build randomness beacons, which are an integral part of Celo's
+[c**·**Labs][CLABS]: We've used drand as the randomness beacon in [**Plumo**](https://medium.com/celoorg/celo-sets-sights-on-becoming-fastest-evm-chain-through-collaboration-with-mysten-labs-e88b426aee83), a SNARK-based ultralight client, and have collaborated with the LoE and have been inspired by the techniques that are used to build randomness beacons, which are an integral part of Celo's
-[Protocol Labs](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Protocol%20Labs%209e18324379574803918146d996c24df5.md): drand is used in the leader election algorithm of the Filecoin protocol. Having a source of bias-resistant entropy is key to the security of Filecoin and therefore, a healthy and secure drand network is of utmost importance for PL.
+[Protocol Labs][PROTOCOL]: drand is used in the leader election algorithm of the Filecoin protocol. Having a source of bias-resistant entropy is key to the security of Filecoin and therefore, a healthy and secure drand network is of utmost importance for PL.
---
### **“Where would you like to see drand two years from now?”**
-[Universidad de Chile](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Universidad%20de%20Chile%2027708a6027104c3ba708e2d8d7508a66.md): We’d like to see drand provide a massively well-known, easy-to-use service on the Internet. It is very important and exciting that drand has left the “academic-sphere” and now provides a useful application to Internet users.
+[Universidad de Chile][CHILE]: We’d like to see drand provide a massively well-known, easy-to-use service on the Internet. It is very important and exciting that drand has left the “academic-sphere” and now provides a useful application to Internet users.
-[ChainSafe Systems](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/ChainSafe%20Systems%20480ac8864a33408dae64fad706c38a8e.md): We would like to see the deployments and usage of drand increase dramatically. Simplifying the onboarding process and establishing incentives for participants will lead to more people deploying drand and participating in randomness networks. As distributed applications grow in number, a strong developer community will help onboard new users and expand the impact of drand to more ecosystems.
+[ChainSafe Systems][CHAINSAFE]: We would like to see the deployments and usage of drand increase dramatically. Simplifying the onboarding process and establishing incentives for participants will lead to more people deploying drand and participating in randomness networks. As distributed applications grow in number, a strong developer community will help onboard new users and expand the impact of drand to more ecosystems.
-[EPFL Center for Digital Trust (C4DT)](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/EPFL%20Center%20for%20Digital%20Trust%20(C4DT)%20dc94bcdadab64950aa1e6bc96cb1e39a.md): Each new partner increases the general trust of the network, so let’s continue expanding the League of Entropy, and scale it to hundreds of nodes. For the onboarding process, a more streamlined and perhaps more asynchronous protocol would really be an enabler for expanding the LoE network.
+[EPFL Center for Digital Trust (C4DT)][C4DT]: Each new partner increases the general trust of the network, so let’s continue expanding the League of Entropy, and scale it to hundreds of nodes. For the onboarding process, a more streamlined and perhaps more asynchronous protocol would really be an enabler for expanding the LoE network.
-[c**·**Labs](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/c%C2%B7Labs%208125559f2fb44804b9e6ca63da70f6b6.md): We hope to see more members join and increase the confidence in the security of the beacon. It will be great to strengthen the resilience of the implementations and have easily accessible tools for consuming and verifying the beacon. We also hope to see it grow to be accepted in important pieces of infrastructure.
+[c**·**Labs][CLABS]: We hope to see more members join and increase the confidence in the security of the beacon. It will be great to strengthen the resilience of the implementations and have easily accessible tools for consuming and verifying the beacon. We also hope to see it grow to be accepted in important pieces of infrastructure.
-[Protocol Labs](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Protocol%20Labs%209e18324379574803918146d996c24df5.md): We are very optimistic about the future of drand! We are eager to welcome more members to the LoE to natively increase the security of the network. We are looking forward to more applications using drand for their protocols and applications. We are working hard to find ways to incentivize the members of the LoE and we welcome ideas from the community. We are integrating many new features in the main drand protocol, such as support for multiple beacons, higher-frequency randomness and time-lock encryption, as also discussed in [drand celebrates One Year as a Randomness Service!](drand%20celebrates%20One%20Year%20as%20a%20Randomness%20Service!%20c66f0a909f034eae8f9bdc1b69d4014b.md) These new features will bring drand ahead of the competition, as it will be able to solve pressing problems, such as “front-running” attacks on decentralized exchanges. Drand is hiring aggressively to increase the capacity of the team and deliver new functionalities faster - come and **join us** if you’re passionate about verifiable, unpredictable and bias-resistant randomness!
+[Protocol Labs][PROTOCOL]: We are very optimistic about the future of drand! We are eager to welcome more members to the LoE to natively increase the security of the network. We are looking forward to more applications using drand for their protocols and applications. We are working hard to find ways to incentivize the members of the LoE and we welcome ideas from the community. We are integrating many new features in the main drand protocol, such as support for multiple beacons, higher-frequency randomness and time-lock encryption, as also discussed in [drand celebrates One Year as a Randomness Service!](/blog/drand-celebrates-one-year-as-a-randomness-service) These new features will bring drand ahead of the competition, as it will be able to solve pressing problems, such as “front-running” attacks on decentralized exchanges. Drand is hiring aggressively to increase the capacity of the team and deliver new functionalities faster - come and **join us** if you’re passionate about verifiable, unpredictable and bias-resistant randomness!
-In short, we are shooting to make drand a foundational protocol for randomness in the Internet, and we are proud of the fact that [drand celebrates One Year as a Randomness Service!](drand%20celebrates%20One%20Year%20as%20a%20Randomness%20Service!%20c66f0a909f034eae8f9bdc1b69d4014b.md), providing more than 1M rounds of randomness!
+In short, we are shooting to make drand a foundational protocol for randomness in the Internet, and we are proud of the fact that [drand celebrates One Year as a Randomness Service!](/blog/drand-celebrates-one-year-as-a-randomness-service), providing more than 1M rounds of randomness!
---
-*[The League of Entropy](https://www.notion.so/The-League-of-Entropy-1e76674b75e249699445799c5083fe78?pvs=21) evaluates, votes on, and onboards new members quarterly. If you want to be a part of the first production-grade distributed randomness beacon and help provide publicly verifiable randomness as a service, contact us at leagueofentropy@googlegroups.com. We are looking for enthusiastic teams with experience running secure production services who are interested in operating drand nodes and relays. We also encourage you to check out the [**drand GitHub repository for details**](https://github.com/drand).*
+*[The League of Entropy][LOE] evaluates, votes on, and onboards new members quarterly. If you want to be a part of the first production-grade distributed randomness beacon and help provide publicly verifiable randomness as a service, contact us at leagueofentropy@googlegroups.com. We are looking for enthusiastic teams with experience running secure production services who are interested in operating drand nodes and relays. We also encourage you to check out the [**drand GitHub repository for details**](https://github.com/drand).*
---
+
+[LOE]: https://drand.love/1e76674b75e249699445799c5083fe78
+[CLOUDFLARE]: https://drand.love/12bbcd90be5f4e42af18599f65019e7e
+[DEDIS]: https://drand.love/e855b8f643d4475aa89a47252e6623d9
+[CHILE]: https://drand.love/27708a6027104c3ba708e2d8d7508a66
+[KUDELSKI]: https://drand.love/d800657770494c6cb39cffb5480407a4
+[PROTOCOL]: https://drand.love/9e18324379574803918146d996c24df5
+[CHAINSAFE]: https://drand.love/480ac8864a33408dae64fad706c38a8e
+[CLABS]: https://drand.love/8125559f2fb44804b9e6ca63da70f6b6
+[C4DT]: https://drand.love/dc94bcdadab64950aa1e6bc96cb1e39a
+[EMERALD]: https://drand.love/e22d8bdb07ef4198b283d0436bcc9cf4
+[EMERALD]: https://drand.love/184fc01bc464488c9570eb543d6c386a
+[PTISP]: https://drand.love/f8fa38c9c36d4b4bbbb40fe785e9ae12
+[TIERION]: https://drand.love/5b38e1b289f44e9d87498eddb788d38f
+[UCL]: https://drand.love/af818bec61a542daa950596f01fddf09
+[QUANTUM]: https://drand.love/b3e60c968098435790c3718f85ed3057
diff --git a/blog/2022-02-20-multi-frequency-support-timelock-encryption.mdx b/blog/2022-02-20-multi-frequency-support-timelock-encryption.mdx
index 2b51f6d2..bc2f37db 100644
--- a/blog/2022-02-20-multi-frequency-support-timelock-encryption.mdx
+++ b/blog/2022-02-20-multi-frequency-support-timelock-encryption.mdx
@@ -1,5 +1,5 @@
---
-slug: "multi-frequency-support-&-timelock-encryption-are-coming-to-drand"
+slug: "multi-frequency-support-and-timelock-encryption-are-coming-to-drand"
title: "Multi-Frequency Support & Timelock Encryption are coming to drand!"
authors: [yolan]
tags: [features]
@@ -75,7 +75,7 @@ It is worth noting that all of the properties already natively integrated in dra
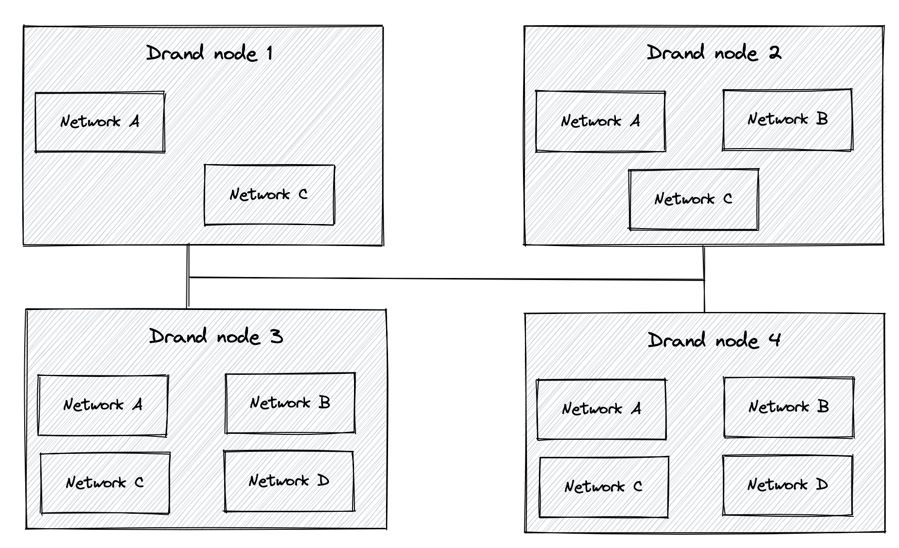
With the updated setup different frequencies (realized as routines) are generated and live within the same process as separate protocols, although each protocol is completely isolated from each other. Applications that wish to consume randomness at some particular frequency can form a separate network. Nodes that join each network participate in randomness generation and propagation between them and make use of the corresponding protocol.
-
+
More generally, each new frequency runs as a separate protocol. The new protocol can also choose between chained and unchained randomness. So, for instance, if we assume that the main drand network (the one operated by the LoE) runs at some specific frequency in unchained randomness mode, one can set up a new network with a different frequency and chained randomness.
diff --git a/blog/2022-03-29-storswift-joins-the-league-of-entropy.md b/blog/2022-03-29-storswift-joins-the-league-of-entropy.md
index 3f3c3410..c4c6df12 100644
--- a/blog/2022-03-29-storswift-joins-the-league-of-entropy.md
+++ b/blog/2022-03-29-storswift-joins-the-league-of-entropy.md
@@ -10,13 +10,13 @@ date: 2022-03-29
-
+
We are excited to announce that [**StorSwift**](https://storswift.com/), a China-based cloud computing and storage services company, is joining forces with the [**League of Entropy**](https://leagueofentropy.com/) (LoE)! StorSwift is becoming the 15th member to join the LoE and the first partner joining from China - a significant milestone for the LoE!
StorSwift has already deployed various workload-scalable enterprise storage systems in video surveillance, HPC, and AI industries and provides support for the many platforms in operation. Based on their extensive experience with large-scale infrastructure projects, StorSwift has recently focused on improving infrastructure management and security techniques for Web3.0 computing platforms - all of which make StorSwift a great addition to the LoE! Welcome!
-We've asked StorSwift some key questions that we've previously asked other LoE members - see [**here**](The%20Value%20of%20drand%20(Part%201%20of%202)%200cc0bb5ecb6d471da62152370180701b.md) and [**here**](The%20Value%20of%20drand%20(Part%202%20of%202)%206d53b4cc6b5f4f31a8cab0b3fe2e94c3.md) - on the value of drand. Here are the answers.
+We've asked StorSwift some key questions that we've previously asked other LoE members - see [**here**](/blog/the-value-of-drand-part-1-of-2) and [**here**](/blog/the-value-of-drand-part-2-of-2) - on the value of drand. Here are the answers.
---
diff --git a/blog/2022-06-23-drand-at-northsec.mdx b/blog/2022-06-23-drand-at-northsec.mdx
index b435132e..cbe61485 100644
--- a/blog/2022-06-23-drand-at-northsec.mdx
+++ b/blog/2022-06-23-drand-at-northsec.mdx
@@ -26,7 +26,7 @@ At North Sec you find plenty of security professionals and hackers alike in the
The Drand team attended North Sec to present a talk titled “Public, verifiable, and unbiasable randomness: wassat?” whose goal was to introduce the different flavours of randomness to the audience, as well as to explain some of the quirks that make randomness a sensitive topic, and why it’s especially difficult in the distributed, public case. Finally, we also did a recap about the current drand network being run by the League of Entropy and available to the public as a source of randomness. We have invited interested parties to start using drand in their projects, or to join the [**League of Entropy**](https://www.cloudflare.com/en-gb/leagueofentropy/) to contribute to a secure, distributed randomness network.
-
+
### **Key Takeaways from the Talk**
@@ -36,7 +36,7 @@ In case you need a refresher or are just curious about what this talk was about,
- **Verifiable randomness is another kind of randomness that can be proven to have been generated in a given (honest) way**. This is useful in order to increase public trust in one’s system. If you run a lottery but nobody knows how you’re choosing the winning number, people might be wary, whereas if you chose the winning numbers by picking them live on TV in a jar, then people can see you’re unlikely to bias the result. In the same way, verifiable randomness aims at increasing trust by providing a means of verifying the random value is unbiased and generated in a fair manner.
- **Secret randomness is the kind of randomness you’re most used to and is meant to stay secret**: every time you connect to a website, every time you generate a new SSH or PGP key, that’s the kind of randomness you’ll be using. For this kind of randomness, you usually want to source it from your very own computer and to rely on so-called “cryptographic PRNGs” when using it in your code to produce nonces, IVs or secret keys. It’s called “secret” because a leak or bias can have devastating consequences up to secret key leakage from a single signature, for example.
-
+
- **Distributed randomness is what we call randomness that is meant to be used on a distributed system;** be it a smart contract on a blockchain, or any other random value on which a system needs to achieve consensus, maybe for leader election, or something else. It’s usually fairly difficult to achieve consensus on a random value in a way that will ensure that this random value is neither predictable nor biased. In general, care must be taken in the distributed case to avoid “[**front-running**](https://en.wikipedia.org/wiki/Front_running)”: if someone can race the distributed system as soon as the random value is public and get their own transaction in just after the random value became public, it might have pretty severe consequences for the system. Therefore, if the public randomness is used to designate a winner, or if there is any potential gain from knowing it before others, we recommend relying on a “locking period” just before public release of the random beacon where you stop accepting new submissions, in order to avoid [**MEV attacks**](https://ethereum.org/en/developers/docs/mev/#effects-of-mev-the-bad) and front-running.
- **drand and the League of Entropy are running a network of nodes providing public, verifiable, distributed randomness** with 100% uptime since its launch in 2020! You can access it freely using our HTTP endpoints:
@@ -48,7 +48,7 @@ In case you need a refresher or are just curious about what this talk was about,
Just don’t forget to verify the randomness and don’t use it to produce secret keys!
-
+
## ❓ **Q&A**
@@ -64,7 +64,7 @@ While we had many interesting questions during the cryptography session panel, h
- **Q: How can an organization join the League of Entropy and run a drand node?**
-**A:** Just [**head to our webpage**](https://www.notion.so/drand-98e192e7414247ff898c4258d4cc28c1?pvs=21) and fill the form at the bottom! The LoE will then discuss the application and if there are no blockers, we’ll get in touch with you, help you setup your node and join our testnet. This is a pre-cautionary, short testing period to make sure everything works fine, after which your node can join the mainnet network! There’s almost no paperwork, and it’s a fairly straightforward process.
+**A:** Just [**head to our webpage**](https://drand.love/) and fill the form at the bottom! The LoE will then discuss the application and if there are no blockers, we’ll get in touch with you, help you setup your node and join our testnet. This is a pre-cautionary, short testing period to make sure everything works fine, after which your node can join the mainnet network! There’s almost no paperwork, and it’s a fairly straightforward process.
- **Q: How does Time lock encryption work?**
@@ -81,7 +81,7 @@ While we had many interesting questions during the cryptography session panel, h
- if no: go back to step 1
```
-
+
## 🥇 **Bonus: A Solution to one of the CTF Challenges**
diff --git a/blog/2022-08-25-observing-randomness.mdx b/blog/2022-08-25-observing-randomness.mdx
index ff50eed2..969a624e 100644
--- a/blog/2022-08-25-observing-randomness.mdx
+++ b/blog/2022-08-25-observing-randomness.mdx
@@ -12,7 +12,7 @@ date: 2022-08-25
### What is drand?
-**Drand** is a public, verifiable, unpredictable, and unbiased randomness beacon. It is based on the idea that to generate randomness in a reliable and trustworthy way, you cannot depend on a single entity to control the infrastructure where it runs. This led us to seek the collaboration of multiple organizations to run their own drand daemons, forming [The League of Entropy](https://www.notion.so/The-League-of-Entropy-1e76674b75e249699445799c5083fe78?pvs=21) (LoE)—a distributed organization where each participating partner runs a drand node.
+**Drand** is a public, verifiable, unpredictable, and unbiased randomness beacon. It is based on the idea that to generate randomness in a reliable and trustworthy way, you cannot depend on a single entity to control the infrastructure where it runs. This led us to seek the collaboration of multiple organizations to run their own drand daemons, forming [The League of Entropy][LOE] (LoE)—a distributed organization where each participating partner runs a drand node.
A drand *network* is composed of multiple *nodes*. Each network generates separate randomness beacons at specific intervals, called *rounds*. The number of nodes on a network is fixed at any given point in time and only changes during a *ceremony*. During the ceremony, a *threshold* is set, which is the minimum number of nodes that need to be connected to the network at any given time for randomness generation to succeed.
@@ -117,3 +117,5 @@ it in the dashboard until the ceremony is finished. We would like to have some w
- [Asynchronous System](https://en.wikipedia.org/wiki/Asynchronous_system)
---
+
+[LOE]: https://drand.love/1e76674b75e249699445799c5083fe78
diff --git a/blog/2022-10-19-cryptosat-takes-drand-to-space.mdx b/blog/2022-10-19-cryptosat-takes-drand-to-space.mdx
index 82353244..5fb9b559 100644
--- a/blog/2022-10-19-cryptosat-takes-drand-to-space.mdx
+++ b/blog/2022-10-19-cryptosat-takes-drand-to-space.mdx
@@ -59,6 +59,6 @@ In May 2022, [CryptoSat launched its first satellite](https://cointelegraph.com/
As mentioned, the time-constrained ISS experiment doesn’t provide full insight into the ongoing operation of a node with spotty connectivity. We need to simulate a participant node that is only occasionally available to participate in beacon generation rounds, simulating the conditions of a satellite that is sometimes out of reach of any ground station.
-The future is bright for this collaboration—not only for the two parties involved but most importantly for the users of drand as a randomness service! Reach out if you have ideas on how to add further value to our upcoming experiments, or if you want to get involved and contribute to drand’s vision. Make sure to join our [**drand Slack workspace**](https://join.slack.com/t/drandworkspace/shared_invite/zt-19u4rf6if-bf7lxIvF2zYn4~TrBwfkiA), or reach out by email at: leagueofentropy [ at ] googlegroups.com.
+The future is bright for this collaboration—not only for the two parties involved but most importantly for the users of drand as a randomness service! Reach out if you have ideas on how to add further value to our upcoming experiments, or if you want to get involved and contribute to drand’s vision. Make sure to join our [**drand Slack workspace**](https://join.slack.com/t/drandworkspace/shared_invite/zt-2p00bn43o-qALTK5RZEIK3I4fIO9h8dQ), or reach out by email at: leagueofentropy [ at ] googlegroups.com.
---
diff --git a/blog/2023-01-22-drand-2022-year-in-review-our-2023-roadmap.mdx b/blog/2023-01-22-drand-2022-year-in-review-our-2023-roadmap.mdx
index 137fb165..515d304c 100644
--- a/blog/2023-01-22-drand-2022-year-in-review-our-2023-roadmap.mdx
+++ b/blog/2023-01-22-drand-2022-year-in-review-our-2023-roadmap.mdx
@@ -24,7 +24,7 @@ One of the highlights of 2022 was the development of some game-changing features
Early in the year, we rolled out unchained randomness and higher frequency beacons on our testnet. These features have shown immense potential, and we’ve been thrilled with their performance. They promise to expand the horizons for drand and the applications using it. We’ve been testing them rigorously, and they’ve been operational for several months now.
-*Want to dive deeper? Check out [Multi-Frequency Support & Timelock Encryption are coming to drand!](Multi-Frequency%20Support%20&%20Timelock%20Encryption%20are%20%205c3651ad243541b698024016ecd24d26.md) for all the details.*
+*Want to dive deeper? Check out [Multi-Frequency Support & Timelock Encryption are coming to drand!](/blog/multi-frequency-support-and-timelock-encryption-are-coming-to-drand) for all the details.*
### ⏱️ Timelock Encryption
@@ -39,7 +39,7 @@ Monitoring and maintaining a robust network is crucial. This year, we made signi
- **Integrated Metrics:** We embedded metrics directly into our codebase, providing a clearer view of the network’s health.
- **New Dashboard:** We built a comprehensive dashboard that gives us a holistic view of nodes before, during, and after resharing ceremonies. This tool has been instrumental in enabling async ceremonies, making the process more flexible for node operators.
-*Curious about the technical details? Read more in [Observing Randomness](Observing%20Randomness%2080ade6b218314dde955b5692473d8c1c.md)*
+*Curious about the technical details? Read more in [Observing Randomness](/blog/observing-randomness)*
---
@@ -49,7 +49,7 @@ One of the most exciting developments of 2022 was our collaboration with CryptoS
We’re not stopping there. Our goal is to have a permanent drand node operating from space, further enhancing the resilience of our network.
-*Read all about this groundbreaking achievement in [CryptoSat takes drand to Space!](CryptoSat%20takes%20drand%20to%20Space!%200d0538c9c0df418a9aacf42859eb079f.md)*
+*Read all about this groundbreaking achievement in [CryptoSat takes drand to Space!](/blog/cryptosat-takes-drand-to-space)*
---
@@ -60,7 +60,7 @@ We’re not stopping there. Our goal is to have a permanent drand node operating
- **New Members:** We welcomed four new members to the League and have several more lined up for consideration in the coming months.
- **Community Engagement:** We presented drand at several high-profile events, including NorthSec, MCH, and DEFCON. These presentations sparked new collaborations and expanded our community.
-Interested in joining the League of Entropy? Learn more at [The League of Entropy](https://www.notion.so/The-League-of-Entropy-1e76674b75e249699445799c5083fe78?pvs=21)
+Interested in joining the League of Entropy? Learn more at [The League of Entropy][LOE]
---
@@ -101,10 +101,12 @@ We’re committed to making drand more user- and developer-friendly. This includ
2023 promises to be a year of growth and innovation. We invite you to join us on this exciting journey. Whether you’re a developer, a potential partner, or just a fan of what we’re doing, we’d love to have you involved.
- **Monitor Our Progress:** here on this blog!
-- **Get Involved:** Join the discussion in the drand Slack workspace through this [invitation link](https://join.slack.com/t/drandworkspace/shared_invite/zt-19u4rf6if-bf7lxIvF2zYn4~TrBwfkiA).
+- **Get Involved:** Join the discussion in the drand Slack workspace through this [invitation link](https://join.slack.com/t/drandworkspace/shared_invite/zt-2p00bn43o-qALTK5RZEIK3I4fIO9h8dQ).
Best wishes for a productive 2023! 🎉
---
Feel free to let us know if you need more adjustments or further details!
+
+[LOE]: https://drand.love/1e76674b75e249699445799c5083fe78
diff --git a/blog/2023-01-26-ipfs-force-joins-the-league-of-entropy.mdx b/blog/2023-01-26-ipfs-force-joins-the-league-of-entropy.mdx
index c1eac81f..476bddcc 100644
--- a/blog/2023-01-26-ipfs-force-joins-the-league-of-entropy.mdx
+++ b/blog/2023-01-26-ipfs-force-joins-the-league-of-entropy.mdx
@@ -14,7 +14,7 @@ We are excited to announce that IPFSForce has joined the League of Entropy!
IPFSForce has focused on technology research and development in blockchain since 2017. With the vision of being Web 3.0’s infrastructure service provider, IPFSForce is working to make storage more efficient, cost-effective, open, and safer. With "Co-built Value, Sharing Honour" as a guiding principle, IPFSForce leverages technologies to empower global communities with high-quality services.
-We've asked IPFSForce some key questions that we've previously asked other LoE members - see [**here**](The%20Value%20of%20drand%20(Part%201%20of%202)%200cc0bb5ecb6d471da62152370180701b.md) and [**here**](The%20Value%20of%20drand%20(Part%202%20of%202)%206d53b4cc6b5f4f31a8cab0b3fe2e94c3.md) - on the value of drand. Check out what they said.
+We've asked IPFSForce some key questions that we've previously asked other LoE members - see [**here**](/blog/the-value-of-drand-part-1-of-2) and [**here**](/blog/the-value-of-drand-part-2-of-2) - on the value of drand. Check out what they said.
---
diff --git a/blog/2023-03-14-automata-network-joins-the-league-of-entropy.mdx b/blog/2023-03-14-automata-network-joins-the-league-of-entropy.mdx
index 7525acfc..6116b6fe 100644
--- a/blog/2023-03-14-automata-network-joins-the-league-of-entropy.mdx
+++ b/blog/2023-03-14-automata-network-joins-the-league-of-entropy.mdx
@@ -10,7 +10,7 @@ We are proud to announce that [Automata Network](https://www.ata.network/), a we
{/* truncate */}
-We’ve asked Automata some key questions that we’ve regularly ask of new LoE members - see [**here**](The%20Value%20of%20drand%20(Part%201%20of%202)%200cc0bb5ecb6d471da62152370180701b.md), [**here**](The%20Value%20of%20drand%20(Part%202%20of%202)%206d53b4cc6b5f4f31a8cab0b3fe2e94c3.md) and [**here**](StorSwift%20joins%20the%20League%20of%20Entropy!%204cfa4cda241e4769a98f410428e93ebf.md) - on the value of drand. Here are the team's answers.
+We’ve asked Automata some key questions that we’ve regularly ask of new LoE members - see [**here**](/blog/the-value-of-drand-part-1-of-2), [**here**](/blog/the-value-of-drand-part-2-of-2) and [**here**](/blog/storswift-joins-the-league-of-entropy) - on the value of drand. Here are the team's answers.
---
diff --git a/blog/2023-03-27-timelock-encryption-is-now-supported-on-drand-mainnet.mdx b/blog/2023-03-27-timelock-encryption-is-now-supported-on-drand-mainnet.mdx
index af74dc6e..eddd8d1b 100644
--- a/blog/2023-03-27-timelock-encryption-is-now-supported-on-drand-mainnet.mdx
+++ b/blog/2023-03-27-timelock-encryption-is-now-supported-on-drand-mainnet.mdx
@@ -42,15 +42,15 @@ In order to understand how the system works, we need to first recall a few thing
First things first, let’s recall that `drand`, which stands for “**distributed randomness**” (and thus pronounced “dee-rand”), is our very own [**open-source software**](https://github.com/drand/drand) meant to create distributed randomness networks. These networks emit **random “beacons” at a given frequency** in a way that you never need to trust any single party in the network, and can ***verify*** that you actually have random values as long as you trust there is **never a threshold number of malicious parties** in the network, thus the security of the threshold BLS signature scheme holds.
-To accomplish this drand relies on the threshold BLS signature scheme and its security proof that tells us BLS signatures are indistinguishable from random ones (in the group of all possible signatures). At each epoch, the members of a drand network work together to create an aggregated BLS signature on the message **m = H(round)}**. An important point here for what comes next is that the **message is predictable** according to the target round at a time T (in other words, there is a mapping between time and round numbers, since the network operates at a fixed frequency), when we’re using drand in the so-called unchained mode that [**we presented in a post last year**](Multi-Frequency%20Support%20&%20Timelock%20Encryption%20are%20%205c3651ad243541b698024016ecd24d26.md).
+To accomplish this drand relies on the threshold BLS signature scheme and its security proof that tells us BLS signatures are indistinguishable from random ones (in the group of all possible signatures). At each epoch, the members of a drand network work together to create an aggregated BLS signature on the message **m = H(round)}**. An important point here for what comes next is that the **message is predictable** according to the target round at a time T (in other words, there is a mapping between time and round numbers, since the network operates at a fixed frequency), when we’re using drand in the so-called unchained mode that [**we presented in a post last year**](/blog/multi-frequency-support-and-timelock-encryption-are-coming-to-drand).
-You can learn more about drand and how it works under the hood in our documentation: [**Cryptography Page**](https://www.notion.so/2-1-Concepts-Cryptography-6b6cea36929e4b1b8ed5b00ad8600081?pvs=21)
+You can learn more about drand and how it works under the hood in our documentation: [**Cryptography Page**](https://docs.drand.love/docs/concepts/2-1-concepts-cryptography)
### **The League of Entropy**
The League of Entropy is a consortium of organisations that decided, back in 2019, to start running a global drand network in order to provide free, unbiased, and verifiable public randomness for anyone to use. Since 2019, the League has been growing steadily, with new members joining it regularly and thus increasing the security and trust we can have in the League. You can read more about the League on Cloudflare’s website: [**https://www.cloudflare.com/leagueofentropy/**](https://www.cloudflare.com/leagueofentropy/)
-As of March 2023, the League is constituted of over 21 drand nodes operated by 18 organisations, with a threshold of over 50%, and you can follow our blog to see when new partners are joining the League: [Blog](../Blog%2083785fc385334bd9b893ae3817f2944a.md)
+As of March 2023, the League is constituted of over 21 drand nodes operated by 18 organisations, with a threshold of over 50%, and you can follow our blog to see when new partners are joining the League: [Blog](https://docs.drand.love/blog)
In case you were worried after reading our paper, know that whenever new members join the League, we conduct a so-called “resharing” of the League’s group secret key using verifiable secret sharing. This means that **the public keys of the drand networks we run never change** and it is not going to cause an incompatibility issue with our timelock scheme.
diff --git a/blog/2023-04-26-randomness-summit-tokyo-2023.mdx b/blog/2023-04-26-randomness-summit-tokyo-2023.mdx
index 789fe8b9..51d8b657 100644
--- a/blog/2023-04-26-randomness-summit-tokyo-2023.mdx
+++ b/blog/2023-04-26-randomness-summit-tokyo-2023.mdx
@@ -16,7 +16,7 @@ The Randomness Summit was a one day conference consisting of talks from a range
### Kickoff Presentation
-- **Speaker:** Patrick McClurg from [Randamu](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Randamu%20e79c7048112749dd9a424a35e959c41a.md)
+- **Speaker:** Patrick McClurg from [Randamu](https://randa.mu/)
- **Topic:** Brief overview of drand's progress since the 2020 Randomness Summit.
### 📽️ Presentations
@@ -37,19 +37,19 @@ The Randomness Summit was a one day conference consisting of talks from a range
- **Speaker:** Luis Brandão from NIST
- **Topic:** Ongoing efforts to standardize randomness beacons and threshold cryptography. Details can be found [**on the NIST website**](https://csrc.nist.gov/projects/interoperable-randomness-beacons).
6. **Scalable Byzantine Fault Tolerance Algorithms**
- - **Speaker:** Matej Pavlovic from the Consensus Lab team at [Protocol Labs](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Protocol%20Labs%209e18324379574803918146d996c24df5.md)
+ - **Speaker:** Matej Pavlovic from the Consensus Lab team at [Protocol Labs][PROTOCOL]
- **Topic:** Latest research into scalable Byzantine fault tolerance algorithms and how randomness can improve their performance characteristics.
7. **Timelock Encryption**
- - **Speaker:** Yolan Romailler from [Randamu](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Randamu%20e79c7048112749dd9a424a35e959c41a.md)
+ - **Speaker:** Yolan Romailler from [Randamu](https://randa.mu/)
- **Topic:** Shortened version of his talk on timelock encryption from the main Real World Crypto conference. The full talk is available on the [**IACR YouTube channel**](https://www.youtube.com/watch?v=Xh849Ij3lhU).
### 🌎 Real-World Applications
1. **Drand Implementation in Rust and No-Code Tool**
- - **Speaker:** Hong Yu from [StorSwift](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/StorSwift%20b4a22d49974e4c0186bb9edf41066e8e.md)
+ - **Speaker:** Hong Yu from [StorSwift](/blog/storswift-joins-the-league-of-entropy)
- **Topic:** Upcoming drand implementation in Rust and a no-code tool for creating smart contracts using timelock encryption.
2. **CLI Tool for Drand and Timelock Encryption**
- - **Speaker:** Thibault Meunier from [Cloudflare](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Cloudflare%2012bbcd90be5f4e42af18599f65019e7e.md)
+ - **Speaker:** Thibault Meunier from [Cloudflare](https://drand.love/12bbcd90be5f4e42af18599f65019e7e)
- **Topic:** New [**CLI tool**](https://github.com/thibmeu/drand-rs) for drand and timelock encryption.
### 📚 Resources
diff --git a/blog/2023-05-25-security-assessment-of-tlock.mdx b/blog/2023-05-25-security-assessment-of-tlock.mdx
index 751ce98d..cbb33d98 100644
--- a/blog/2023-05-25-security-assessment-of-tlock.mdx
+++ b/blog/2023-05-25-security-assessment-of-tlock.mdx
@@ -6,13 +6,13 @@ tags: [news, updates]
date: 2023-05-25
---
-We are happy to announce that our timed release encryption scheme "[**tlock**](https://eprint.iacr.org/2023/189)" and its implementations, which we introduced in our [**previous blog post**](Timelock%20Encryption%20is%20now%20supported%20on%20drand%20main%20327425b1e16d4c22aa0d785dbf1c5fbb.md), have recently undergone a comprehensive security assessment by [Kudelski Security](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Kudelski%20Security%20d800657770494c6cb39cffb5480407a4.md). This was a crucial step in ensuring the robustness and reliability of our encryption system in order to guarantee that timelocked content remains encrypted until the time has come for it to be decrypted and never before.
+We are happy to announce that our timed release encryption scheme "[**tlock**](https://eprint.iacr.org/2023/189)" and its implementations, which we introduced in our [**previous blog post**](/blog/timelock-encryption-is-now-supported-on-drand-mainnet), have recently undergone a comprehensive security assessment by [Kudelski Security](https://drand.love/d800657770494c6cb39cffb5480407a4). This was a crucial step in ensuring the robustness and reliability of our encryption system in order to guarantee that timelocked content remains encrypted until the time has come for it to be decrypted and never before.
{/* truncate */}
## **Overview**
-[Kudelski Security](../The%20League%20of%20Entropy%201e76674b75e249699445799c5083fe78/League%20Partners%2089fecb56737044e5bdfbbb3f6864a422/Kudelski%20Security%20d800657770494c6cb39cffb5480407a4.md), a renowned provider of cybersecurity solutions, was engaged to review the implementation of drand’s timelock encryption scheme and timelock responsible disclosure demo. The work covered:
+[Kudelski Security](https://drand.love/d800657770494c6cb39cffb5480407a4), a renowned provider of cybersecurity solutions, was engaged to review the implementation of drand’s timelock encryption scheme and timelock responsible disclosure demo. The work covered:
- `tlock`, our [**Go implementation](https://github.com/drand/tlock/)** as both a library and a command line tool (`tle`) for timelock encryption.
- `tlock-js`, our interoperable [**TypeScript implementation](https://github.com/drand/tlock-js/)** of timelock encryption.
diff --git a/blog/2023-06-01-drand-explainer-for-beginners.mdx b/blog/2023-06-01-drand-explainer-for-beginners.mdx
index d0bf188e..4c509daa 100644
--- a/blog/2023-06-01-drand-explainer-for-beginners.mdx
+++ b/blog/2023-06-01-drand-explainer-for-beginners.mdx
@@ -97,7 +97,7 @@ At the foundation of a drand network, all parties generate their own private key
This was a whistle-stop tour of how drand works, and some details were omitted for clarity.
-If you'd like to dive deeper into the cryptography or operation of the drand network, check out our [**documentation**](https://www.notion.so/2-0-CONCEPTS-Getting-Started-22d96de1674b448599227c37a1df5379?pvs=21), [**join our Slack workspace**](https://join.slack.com/t/drandworkspace/shared_invite/zt-19u4rf6if-bf7lxIvF2zYn4~TrBwfkiA), or email us at: [leagueofentropy@googlegroups.com](mailto:leagueofentropy@googlegroups.com).
+If you'd like to dive deeper into the cryptography or operation of the drand network, check out our [**documentation**](https://docs.drand.love/docs/category/20-concepts-getting-started), [**join our Slack workspace**](https://join.slack.com/t/drandworkspace/shared_invite/zt-19u4rf6if-bf7lxIvF2zYn4~TrBwfkiA), or email us at: [leagueofentropy@googlegroups.com](mailto:leagueofentropy@googlegroups.com).
---
diff --git a/blog/2023-06-05-announcing-the-drand-code-walkthroughs.md b/blog/2023-06-05-announcing-the-drand-code-walkthroughs.md
index d9d77612..779bccaf 100644
--- a/blog/2023-06-05-announcing-the-drand-code-walkthroughs.md
+++ b/blog/2023-06-05-announcing-the-drand-code-walkthroughs.md
@@ -6,7 +6,6 @@ tags: [news, how-to, code-walkthrough]
date: 2023-06-05
---
-test

## **What, Where, & When**
diff --git a/blog/2023-07-02-fastnet-to-be-sunset-long-live-quicknet.md b/blog/2023-07-02-fastnet-to-be-sunset-long-live-quicknet.md
index e483d422..f8ed06fb 100644
--- a/blog/2023-07-02-fastnet-to-be-sunset-long-live-quicknet.md
+++ b/blog/2023-07-02-fastnet-to-be-sunset-long-live-quicknet.md
@@ -14,7 +14,7 @@ Last month, we have identified [**a minor issue](https://github.com/drand/kyber
While not a *security issue* for drand, the problem is affecting our “hash to curve” function, used to map round numbers to a point on the elliptic curve that get signed using [**threshold BLS](https://en.wikipedia.org/wiki/BLS_digital_signature)** by the drand network. The issue relates to the upcoming Hash To Curve [**RFC 9380**](https://www.rfc-editor.org/auth48/rfc9380), which mandates specific “Domain Separation Tags“ (DST) for certain curves. In the BLS curve case, where we have two different groups (G1 and G2) that we can map to, the RFC recommends using different DST for both groups (it’s the point of having a DST!). Sadly, our implementation of BLS signatures was initially written to perform signatures on G2 and not on G1… (Stay tuned for an upcoming blog post about the choice of the group for BLS signatures!) The usage of a global variable in our codebase for the DST meant that both our G1 and G2 implementations were sharing the same DST. Since we don’t have “official test vectors” for BLS signatures on G1 and G2, this went unnoticed until [**someone tried](https://drandworkspace.slack.com/archives/C011JB8NU2E/p1683527867397549?thread_ts=1683197659.071499&cid=C011JB8NU2E)** to verify our signatures done on G1 with a C++ implementation and reported the issue in our Slack.
-We launched our `fastnet` Testnet in February to try and identify any potential issues, while also allowing people to start building their applications on top of our new design featuring [**unchained randomness**](https://www.notion.so/2-1-Concepts-Cryptography-6b6cea36929e4b1b8ed5b00ad8600081?pvs=21) and [**timelock capabilities**](Timelock%20Encryption%20is%20now%20supported%20on%20drand%20main%20327425b1e16d4c22aa0d785dbf1c5fbb.md). Despite this, the issue went unnoticed in all signature verification implementations that we tried with our drand beacons (including our typescript [**drand-client](https://github.com/drand/drand-client)** codebase and two different third party Rust implementations of drand verification!). Amusingly, within weeks of this issue being identified, a second team, building their own timelock scheme on top of our new `fastnet` network, also identified the issue and reported it to us.
+We launched our `fastnet` Testnet in February to try and identify any potential issues, while also allowing people to start building their applications on top of our new design featuring [**unchained randomness**](https://docs.drand.love/docs/concepts/2-1-concepts-cryptography) and [**timelock capabilities**](/blog/timelock-encryption-is-now-supported-on-drand-mainnet). Despite this, the issue went unnoticed in all signature verification implementations that we tried with our drand beacons (including our typescript [**drand-client](https://github.com/drand/drand-client)** codebase and two different third party Rust implementations of drand verification!). Amusingly, within weeks of this issue being identified, a second team, building their own timelock scheme on top of our new `fastnet` network, also identified the issue and reported it to us.
For us, the main takeaways here are:
@@ -35,10 +35,10 @@ During investigations, we identified 4 main ways to solve this issue:
- **Create a new** `fastnet` **network (`quicknet`)** using a **compliant implementation** of the signature function and **shutdown** the existing non-compliant one immediately. This would inevitably cause our current `fastnet` users to be completely stranded and having to switch quickly to our new `quicknet` network, causing serious disruption for our users.
- **Create a new** `quicknet` **network** using a **compliant implementation** of the signature function and **sunset** the existing one over multiple months before **shutting it down entirely**. This would allow our users to ensure 100% uptime of their services, while gradually migrating to the new network.
-Given the above, [The League of Entropy](https://www.notion.so/The-League-of-Entropy-1e76674b75e249699445799c5083fe78?pvs=21) has voted and elected to choose the last option, using its governance process, and therefore will:
+Given the above, [The League of Entropy][LOE] has voted and elected to choose the last option, using its governance process, and therefore will:
- **Sunset** the current `fastnet` network, reduce the number of Mainnet nodes running it (from 21 with a **threshold of 11** to a committee of 14 with a **threshold of 8**), stop onboarding new nodes to it, and most importantly **stop it entirely** as soon as possible.
-- launch a new `quicknet` network with the same settings, e.g. 3 seconds frequency, 2 seconds catch-up period, [**unchained randomness](Multi-Frequency%20Support%20&%20Timelock%20Encryption%20are%20%205c3651ad243541b698024016ecd24d26.md)** (thus compatible with timelock schemes), except it would be using our newly released `bls-unchained-g1-rfc9380` scheme which is RFC-compliant.
+- launch a new `quicknet` network with the same settings, e.g. 3 seconds frequency, 2 seconds catch-up period, [**unchained randomness](/blog/multi-frequency-support-and-timelock-encryption-are-coming-to-drand)** (thus compatible with timelock schemes), except it would be using our newly released `bls-unchained-g1-rfc9380` scheme which is RFC-compliant.
- do the same on our Testnet `testnet-g` network, shutting it down before Mainnet, in order to allow us to effectively test the shutdown scenario.
We are currently planning to launch these new `quicknet` networks in July on both our Testnet and Mainnet.
diff --git a/blog/2023-10-15-quicknet-is-live-on-League-of-Entropy-mainnet.md b/blog/2023-10-15-quicknet-is-live-on-League-of-Entropy-mainnet.md
index 5d9f27e7..3506d6a1 100644
--- a/blog/2023-10-15-quicknet-is-live-on-League-of-Entropy-mainnet.md
+++ b/blog/2023-10-15-quicknet-is-live-on-League-of-Entropy-mainnet.md
@@ -50,7 +50,7 @@ The same holds for our testnet relays, e.g. [https://pl-us.testnet.drand.sh/chai
- `f3827d772c155f95a9fda8901ddd59591a082df5ac6efe3a479ddb1f5eeb202c` our `testnet-g` unchained beacon chain, featuring our non-RFC compliant G1 signature scheme.
- `cc9c398442737cbd141526600919edd69f1d6f9b4adb67e4d912fbc64341a9a5` which is our latest `quicknet-t` network, featuring RFC compliant BLS12-381 G1 based BLS signatures!
-Check our [DevGuide: HTTP API](https://www.notion.so/3-4-DevGuide-HTTP-API-12e8a9712c5b4b77a52e2b42de1ac009?pvs=21) for more information about our public endpoints!
+Check our [DevGuide: HTTP API](https://docs.drand.love/docs/dev-guide/3-4-dev-guide-http-api) for more information about our public endpoints!
## `quicknet-t`
@@ -88,9 +88,9 @@ The same holds for our mainnet relays. Any given beacon chain information can be
## Sun-setting of `fastnet`
-If you've been following our blog, you'll remember our previous post about [Timelock Encryption is now supported on drand mainnet](Timelock%20Encryption%20is%20now%20supported%20on%20drand%20main%20327425b1e16d4c22aa0d785dbf1c5fbb.md) where we announced the launch of our new `fastnet` network that supported our timelock scheme. The League of Entropy launched this new drand network on March 1st, 2023. However, we quickly identified an issue with our BLS signatures on G1 that made them non-compliant with the Hash To Curve [RFC 9380](https://www.ietf.org/rfc/rfc9380.html) specification, as well as most BLS signatures implementations on G1 apart from ours. Therefore, we had to double down and launch the `quicknet` network to fix this issue.
+If you've been following our blog, you'll remember our previous post about [Timelock Encryption is now supported on drand mainnet](/blog/timelock-encryption-is-now-supported-on-drand-mainnet) where we announced the launch of our new `fastnet` network that supported our timelock scheme. The League of Entropy launched this new drand network on March 1st, 2023. However, we quickly identified an issue with our BLS signatures on G1 that made them non-compliant with the Hash To Curve [RFC 9380](https://www.ietf.org/rfc/rfc9380.html) specification, as well as most BLS signatures implementations on G1 apart from ours. Therefore, we had to double down and launch the `quicknet` network to fix this issue.
-We’ll be sun-setting `fastnet` in the coming months [as announced previously](https://drand.love/blog/2023/07/03/fastnet-sunset-quicknet-new/). We are currently going to scale down `fastnet` by another 3 nodes in November, and we’ll be shutting it down completely at the earliest opportunity. Please reach out to
+We’ll be sun-setting `fastnet` in the coming months [as announced previously](/blog/fastnet-to-be-sunset). We are currently going to scale down `fastnet` by another 3 nodes in November, and we’ll be shutting it down completely at the earliest opportunity. Please reach out to
us if this is a concern for you or your team.
@@ -99,15 +99,15 @@ us if this is a concern for you or your team.
## Shoutout to the League of Entropy 🤝
-Our decentralization journey wouldn't be possible without [The League of Entropy](https://www.notion.so/The-League-of-Entropy-1e76674b75e249699445799c5083fe78?pvs=21). We are delighted to share that all members in the League of Entropy are running the `quicknet` drand network alongside the `default` chained beacon network on the League’s network of 23 nodes.
+Our decentralization journey wouldn't be possible without [The League of Entropy][LOE]. We are delighted to share that all members in the League of Entropy are running the `quicknet` drand network alongside the `default` chained beacon network on the League’s network of 23 nodes.
A big shoutout to the League of Entropy for their invaluable contributions, running drand nodes for free for anyone to use whenever one needs public, verifiable randomness. Together, we're pioneering a faster, more decentralized future for randomness generation, with this new unchained network enabling a host of new possibilities for our users!
## Get Started 🚀
-For developers and users eager to dive into the new `quicknet` drand network, our [official documentation](https://drand.love/developer/) provides detailed resources about using drand relays and beacons.
+For developers and users eager to dive into the new `quicknet` drand network, our [official documentation](https://docs.drand.love/docs/category/30-developers-guide) provides detailed resources about using drand relays and beacons.
-We also have a blog post about “[drand for beginners](https://drand.love/blog/2023/06/02/drand-explainer/)” that’s packed with useful information and another one about [using drand on-chain](https://drand.love/blog/2023/03/16/draffle/) with a demo lottery use-case running on the Filecoin Virtual Machine.
+We also have a blog post about “[drand for beginners](/blog/drand-explainer-for-begginers)” that’s packed with useful information and another one about [using drand on-chain](/blog/drand-on-filecoin-virtual-machine-FVM-draffle) with a demo lottery use-case running on the Filecoin Virtual Machine.
## G1 - G2 Swap
@@ -127,7 +127,7 @@ This swap allowed us to **reduce the size of the drand beacons emitted by the ne
## Unchained Mode
-We’ve introduced the notion of [unchained beacons](https://drand.love/blog/2022/02/21/multi-frequency-support-and-timelock-encryption-capabilities/#unchained-randomness-timed-encryption) last year on the blog already. But in essence, the new drand network brings a host of improvements aimed at enhancing the overall UX for drand users and developers. The 'unchained mode' means that new random beacons are entirely independent from previous ones, meaning that you can now perform stateless verification of a beacon, without having to keep a record of past beacons!
+We’ve introduced the notion of [unchained beacons](/blog/multi-frequency-support-and-timelock-encryption-are-coming-to-drand) last year on the blog already. But in essence, the new drand network brings a host of improvements aimed at enhancing the overall UX for drand users and developers. The 'unchained mode' means that new random beacons are entirely independent from previous ones, meaning that you can now perform stateless verification of a beacon, without having to keep a record of past beacons!
These enhancements are designed to make the drand network more robust, efficient, and user-friendly. They help in reducing the computational and storage load of our users, making drand more cost-effective and faster. The unchained nature of the beacons also means you can now decide to sample only one every 5 beacons to have a frequency of 15s or one every 20 beacons to have a frequency of 1 minute! This significantly improves flexibility and scalability for everyone.
@@ -145,7 +145,7 @@ The fact that the drand beacons are now **unchained** might give the *false impr
- **Predictability:** An attacker controlling a threshold number of shares is able to predict any arbitrary round in the unchained setting, whereas they would need to compute all intermediary rounds to predict a given future round with the chained setting. *However*, controlling a threshold amount of shares at any point in time allows computation of the shared secret of the group, and nothing can prevent such an attacker having obtained the group secret from then computing all future chained rounds offline much faster than the existing network would have, leading to the same result as in the unchained case: complete predictability of all future rounds in case of a compromise of either scheme.
- **Bias:** All future beacons are entirely determined by two things: the initial Distributed Key Generation and their round number. This was already the case for the chained network and hasn’t changed with the unchained schemes. For a given distributed group public key, future rounds cannot be biased in any way after the initial Distributed Key Generation ceremony has been run.
-We’ve also made sure our new Timelock Encryption service relying on our new `quicknet` network was [properly audited](https://drand.love/blog/2023/05/26/tlock-security-assessment/). We’ve got you covered!
+We’ve also made sure our new Timelock Encryption service relying on our new `quicknet` network was [properly audited](/blog/security-assessment-of-tlock). We’ve got you covered!
## Extra Liveness!
@@ -162,3 +162,5 @@ If you are already doing so, or plan on doing so, don’t hesitate to join our [
Until next time! 😄
---
+
+[LOE]: https://drand.love/1e76674b75e249699445799c5083fe78
diff --git a/blog/2024-07-26-creating-a-notion-widget-to-display-the-latest-pub.md b/blog/2024-07-26-creating-a-notion-widget-to-display-the-latest-pub.md
index 4342fd20..ebe0889f 100644
--- a/blog/2024-07-26-creating-a-notion-widget-to-display-the-latest-pub.md
+++ b/blog/2024-07-26-creating-a-notion-widget-to-display-the-latest-pub.md
@@ -15,7 +15,7 @@ In this blog post, we’ll dive into creating a simple Notion widget that displa
## An overview of drand
-Our earlier [blog](https://drand.love/blog/a-guide-on-how-to-use-drand) post titled "A Guide on How to Use drand", explains the importance of public randomness and how drand provides it using a threshold network. It offers a step-by-step tutorial on setting up and using drand's randomness in applications, including fetching randomness with JavaScript, verifying it, and using it in real-life scenarios like coin flips and random selection. The guide emphasizes fairness and verifiability in applications requiring random numbers.
+Our earlier [blog](/blog/a-guide-on-how-to-use-drand) post titled "A Guide on How to Use drand", explains the importance of public randomness and how drand provides it using a threshold network. It offers a step-by-step tutorial on setting up and using drand's randomness in applications, including fetching randomness with JavaScript, verifying it, and using it in real-life scenarios like coin flips and random selection. The guide emphasizes fairness and verifiability in applications requiring random numbers.
In a nutshell, drand uses a threshold network, where multiple parties collaborate to generate random numbers, ensuring no single entity can predict or bias the outcome. By leveraging hashed signatures without a complete secret key held by any party, drand achieves verifiable randomness. This system's reliability and unpredictability make it ideal for projects with a dependency on secure and verifiable randomness.
@@ -37,7 +37,7 @@ npm install drand-client
Once the drand client is installed, we’re ready to start implementing our simple ReactJS application! The application will allow users to select their desired network (i.e., default or quicknet) from a dropdown menu and display the latest randomness after each round, the round number and a countdown to the next randomness generation round or ETA.
-Appropriate API URLs for the mainnet default and quicknet networks can be found here: [https://drand.love/docs/developers-guide](https://drand.love/docs/developers-guide)
+Appropriate API URLs for the mainnet default and quicknet networks can be found here: [https://docs.drand.love/docs/dev-guide/3-0-dev-guide](https://docs.drand.love/docs/dev-guide/3-0-dev-guide)
Let’s implement the reactjs component in our `App.js` file.
diff --git a/blog/2024-09-14-fastnet-sunsetting-dates-set.mdx b/blog/2024-09-14-fastnet-sunsetting-dates-set.mdx
index 1842d5b4..36e6b5fa 100644
--- a/blog/2024-09-14-fastnet-sunsetting-dates-set.mdx
+++ b/blog/2024-09-14-fastnet-sunsetting-dates-set.mdx
@@ -44,7 +44,7 @@ Note that the network will continue to operate without disturbance during this t
## Effect on timelocked ciphertexts
-As you may know, the League of Entropy `fastnet` and `quicknet` networks both enable you to timelock messages that cannot be decrypted until a given beacon round has been emitted by the network. You can read more about timelock in [our documentation](https://drand.love/docs/timelock-encryption).
+As you may know, the League of Entropy `fastnet` and `quicknet` networks both enable you to timelock messages that cannot be decrypted until a given beacon round has been emitted by the network. You can read more about timelock in [our documentation](https://docs.drand.love/docs/concepts/2-4-concepts-timelock-encryption).
The destruction of all key material related to the `fastnet` network has the unfortunate side-effect of preventing ciphertexts that were timelocked using it towards later dates to ever be decryptable.
diff --git a/blog/authors.yml b/blog/authors.yml
index 0aeb587a..753c8fe6 100644
--- a/blog/authors.yml
+++ b/blog/authors.yml
@@ -1,48 +1,3 @@
-yangshun:
- name: Yangshun Tay
- title: Front End Engineer @ Facebook
- url: https://github.com/yangshun
- image_url: https://github.com/yangshun.png
- page: true
- socials:
- x: yangshunz
- github: yangshun
-
-slorber:
- name: Sébastien Lorber
- title: Docusaurus maintainer
- url: https://sebastienlorber.com
- image_url: https://github.com/slorber.png
- page:
- # customize the url of the author page at /blog/authors/
- permalink: '/all-sebastien-lorber-articles'
- socials:
- x: sebastienlorber
- linkedin: sebastienlorber
- github: slorber
- newsletter: https://thisweekinreact.com
-
-kentbull:
- name: Kent Bull
- title: drand Community Manager
- url: https://kentbull.com
- image_url: https://avatars.githubusercontent.com/u/65027257?v=4
- page: true
- socials:
- x: kentopbull
- github: kentbull
-
-dgrantham:
- name: Dave Grantham
- title: drand Community Manager & Cryptographer
- url: https://cryptid.tech
- image_url: https://avatars.githubusercontent.com/u/5017470?v=4
- page:
- # customize the url of the author page at /blog/authors/
- permalink: '/all-dave-grantham-articles'
- socials:
- github: dhuseby
-
yolan:
name: Yolan Romailler
title: Co-Founder & Cryptographer
@@ -52,7 +7,7 @@ yolan:
Worked on the Distributed Randomness project, drand, at Protocol Labs and also on CBDC and SSI at SICPA, as well as broader cryptographic engineering at Kudelski Security. I've also been a Security Engineer on the Diem security team for Novi (Facebook/Meta).
A subject matter expert in secure coding. As a consultant, I've supported customers by answering complex questions on security critical systems such as blockchain technologies, and by designing, evaluating and implementing complex cryptography such as key management systems or cryptographic primitives.
url: https://romailler.ch/
- image_url: https://media.licdn.com/dms/image/v2/C5603AQHKMl2eqMuNaw/profile-displayphoto-shrink_200_200/profile-displayphoto-shrink_200_200/0/1587563958538?e=1731542400&v=beta&t=P3xWRN9Vxshih2vPsvbdBKWmBo8mH5rTQGQljBlMEYg
+ image_url: /img/author/yolan.jpeg
page: true
socials:
linkedin: anomalroil
@@ -65,7 +20,7 @@ patrick:
description: |
Randamu, drand, threshold cryptography
Polyglot developer
- image_url: https://media.licdn.com/dms/image/v2/D4E03AQHnR3WKvq1g2A/profile-displayphoto-shrink_200_200/profile-displayphoto-shrink_200_200/0/1709586991713?e=1731542400&v=beta&t=ea_E7RBxxyUtNewe_LAF9GvvFd3FzFiIufckhXM4Dps
+ image_url: /img/author/patrick.jpeg
page: true
socials:
linkedin: patrickmcclurg
@@ -76,7 +31,7 @@ laith:
title: Fullstack & DevOps Engineer
description: |
I'm a full stack software engineer & devops who loves to build systems and pipelines meticulously. I care about attention to detail, correctness, and maintainability.
- image_url: https://media.licdn.com/dms/image/v2/C4E03AQEgjfh_7ZwmSw/profile-displayphoto-shrink_200_200/profile-displayphoto-shrink_200_200/0/1516525202814?e=1731542400&v=beta&t=J4YvtoE2WK49MXtUylIv4xoUq9W9i3u07GkUq78yHwI
+ image_url: /img/author/laith.jpeg
page: true
socials:
linkedin: laith-alissa-b2760874
@@ -86,8 +41,7 @@ erick:
title: Co-Founder & CEO @ Randamu | Decentralized Ecosystem Builder
description: |
Erick Watson serves as the CEO of Randamu, a company that specializes in developing leading-edge cryptographic solutions. With over 15 years of experience in leading innovation projects, Erick has a proven track record of delivering value to customers and stakeholders.
- image_url: https://media.licdn.com/dms/image/v2/D5603AQFDZrnupQzeLg/profile-displayphoto-shrink_200_200/profile-displayphoto-shrink_200_200/0/1718309668467?e=1731542400&v=beta&t=kgfROyBEDKJRwqnxhOYRKzOWMOlhNEz9lTeU-SGofJQ
+ image_url: /img/author/erick.jpeg
socials:
linkedin: erick-watson
website: https://randa.mu
-
diff --git a/docs/01_about/01-00-about.md b/docs/01_about/01-00-about.md
index bcca01cb..5363a88a 100644
--- a/docs/01_about/01-00-about.md
+++ b/docs/01_about/01-00-about.md
@@ -38,7 +38,7 @@ drand generates randomness without allowing any party to predict or bias the out
1. **Network Setup**: A drand network consists of nodes running the drand protocol. These nodes agree on a threshold parameter and generate partial signatures.
2. **Randomness Generation**: Nodes broadcast parts of their signatures, which are collected until they match the threshold. The final signature, a [**Boneh–Lynn–Shacham**](https://en.wikipedia.org/wiki/BLS_digital_signature) (BLS) signature, is verified by the network and hashed to produce the random value.
-For more details, refer to the [project specifications](https://drand.love/docs/specification).
+For more details, refer to the [project specifications](https://docs.drand.love/docs/concepts/2-3-concepts-specification).
## Public Randomness
diff --git a/docs/03_dev-guide/03-00-DEVELOPERS_GUIDE.md b/docs/03_dev-guide/03-00-DEVELOPERS_GUIDE.md
index 9b1a957c..76f1a729 100644
--- a/docs/03_dev-guide/03-00-DEVELOPERS_GUIDE.md
+++ b/docs/03_dev-guide/03-00-DEVELOPERS_GUIDE.md
@@ -28,7 +28,7 @@ There are two networks on mainnet:
`quicknet` network chain hash: `52db9ba70e0cc0f6eaf7803dd07447a1f5477735fd3f661792ba94600c84e971`
@@ -42,4 +42,4 @@ Alternatively, you can interact directly with the endpoints. Make sure to manual
Finally, for development purposes, we recommend also testing your code against our Testnet endpoints. See [**our dedicated documentation entry about testnet endpoints**](3-4-dev-guide-http-api).
----
\ No newline at end of file
+---
diff --git a/docs/03_dev-guide/03-04-DevGuide_HTTP_API.md b/docs/03_dev-guide/03-04-DevGuide_HTTP_API.md
index 7d5735ab..1570b0c0 100644
--- a/docs/03_dev-guide/03-04-DevGuide_HTTP_API.md
+++ b/docs/03_dev-guide/03-04-DevGuide_HTTP_API.md
@@ -38,7 +38,7 @@ The chain hash for the League of Entropy `quicknet` network running at a 3s fr
52db9ba70e0cc0f6eaf7803dd07447a1f5477735fd3f661792ba94600c84e971
```
-Note that [**the `fastnet`](https://drand.love/blog/2023/07/03/fastnet-sunset-quicknet-new/) [network has been deprecated.](https://www.notion.so/fastnet-to-be-sunset-long-live-quicknet-5d125025752146b5bc307c834435d49e?pvs=21)**
+Note that [**the `fastnet`](/blog/fastnet-to-be-sunset) [network has been deprecated.](https://www.notion.so/fastnet-to-be-sunset-long-live-quicknet-5d125025752146b5bc307c834435d49e?pvs=21)**
### **Testnet endpoints**
@@ -133,4 +133,4 @@ Retrieves a previous round of randomness identified by the positive integer `ro
**Note**: For backwards-compatibility reasons, paths without `chain-hash` will resort to the the default network in operation.
----
\ No newline at end of file
+---
diff --git a/docusaurus.config.ts b/docusaurus.config.ts
index d2276bd3..7755fe1d 100644
--- a/docusaurus.config.ts
+++ b/docusaurus.config.ts
@@ -129,6 +129,7 @@ const config: Config = {
prism: {
theme: prismThemes.github,
darkTheme: prismThemes.dracula,
+ additionalLanguages: ['solidity', 'java', 'rust', 'jsx', 'bash', 'protobuf']
},
} satisfies Preset.ThemeConfig,
};
diff --git a/static/img/author/erick.jpeg b/static/img/author/erick.jpeg
new file mode 100644
index 00000000..2eae17b1
Binary files /dev/null and b/static/img/author/erick.jpeg differ
diff --git a/static/img/author/laith.jpeg b/static/img/author/laith.jpeg
new file mode 100644
index 00000000..017d1783
Binary files /dev/null and b/static/img/author/laith.jpeg differ
diff --git a/static/img/author/patrick.jpeg b/static/img/author/patrick.jpeg
new file mode 100644
index 00000000..bc2234ba
Binary files /dev/null and b/static/img/author/patrick.jpeg differ
diff --git a/static/img/author/yolan.jpeg b/static/img/author/yolan.jpeg
new file mode 100644
index 00000000..0c971e48
Binary files /dev/null and b/static/img/author/yolan.jpeg differ
diff --git a/static/img/Untitled3.229cc637.jpeg b/static/img/biased-randomness.jpeg
similarity index 100%
rename from static/img/Untitled3.229cc637.jpeg
rename to static/img/biased-randomness.jpeg
diff --git a/static/img/multi-frequency-diagram.avif b/static/img/multi-frequency-diagram.avif
new file mode 100644
index 00000000..c19ee7b0
Binary files /dev/null and b/static/img/multi-frequency-diagram.avif differ
diff --git a/static/img/Untitled.900a032c.jpg b/static/img/northsec-presentation-01.jpg
similarity index 100%
rename from static/img/Untitled.900a032c.jpg
rename to static/img/northsec-presentation-01.jpg
diff --git a/static/img/Untitled1.225dcd21.jpg b/static/img/northsec-presentation-02.jpg
similarity index 100%
rename from static/img/Untitled1.225dcd21.jpg
rename to static/img/northsec-presentation-02.jpg
diff --git a/static/img/Untitled2.dd2ef53e.jpg b/static/img/northsec-presentation-03.jpg
similarity index 100%
rename from static/img/Untitled2.dd2ef53e.jpg
rename to static/img/northsec-presentation-03.jpg